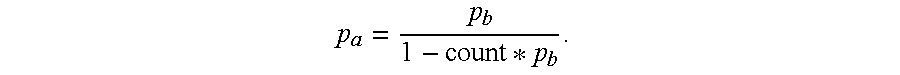US6744767B1 - Method and apparatus for provisioning and monitoring internet protocol quality of service - Google Patents
Method and apparatus for provisioning and monitoring internet protocol quality of service Download PDFInfo
- Publication number
- US6744767B1 US6744767B1 US09/475,512 US47551299A US6744767B1 US 6744767 B1 US6744767 B1 US 6744767B1 US 47551299 A US47551299 A US 47551299A US 6744767 B1 US6744767 B1 US 6744767B1
- Authority
- US
- United States
- Prior art keywords
- bandwidth
- service
- packets
- class
- primary
- Prior art date
- Legal status (The legal status is an assumption and is not a legal conclusion. Google has not performed a legal analysis and makes no representation as to the accuracy of the status listed.)
- Expired - Fee Related
Links
Images
Classifications
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L45/00—Routing or path finding of packets in data switching networks
- H04L45/12—Shortest path evaluation
- H04L45/123—Evaluation of link metrics
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L45/00—Routing or path finding of packets in data switching networks
- H04L45/22—Alternate routing
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L45/00—Routing or path finding of packets in data switching networks
- H04L45/24—Multipath
- H04L45/247—Multipath using M:N active or standby paths
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L45/00—Routing or path finding of packets in data switching networks
- H04L45/30—Routing of multiclass traffic
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/10—Flow control; Congestion control
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/10—Flow control; Congestion control
- H04L47/20—Traffic policing
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/10—Flow control; Congestion control
- H04L47/24—Traffic characterised by specific attributes, e.g. priority or QoS
- H04L47/2408—Traffic characterised by specific attributes, e.g. priority or QoS for supporting different services, e.g. a differentiated services [DiffServ] type of service
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/10—Flow control; Congestion control
- H04L47/29—Flow control; Congestion control using a combination of thresholds
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/10—Flow control; Congestion control
- H04L47/30—Flow control; Congestion control in combination with information about buffer occupancy at either end or at transit nodes
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/10—Flow control; Congestion control
- H04L47/32—Flow control; Congestion control by discarding or delaying data units, e.g. packets or frames
- H04L47/326—Flow control; Congestion control by discarding or delaying data units, e.g. packets or frames with random discard, e.g. random early discard [RED]
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/50—Queue scheduling
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/50—Queue scheduling
- H04L47/52—Queue scheduling by attributing bandwidth to queues
- H04L47/521—Static queue service slot or fixed bandwidth allocation
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/50—Queue scheduling
- H04L47/62—Queue scheduling characterised by scheduling criteria
- H04L47/622—Queue service order
- H04L47/6225—Fixed service order, e.g. Round Robin
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/50—Queue scheduling
- H04L47/62—Queue scheduling characterised by scheduling criteria
- H04L47/625—Queue scheduling characterised by scheduling criteria for service slots or service orders
- H04L47/6265—Queue scheduling characterised by scheduling criteria for service slots or service orders past bandwidth allocation
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/70—Admission control; Resource allocation
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/70—Admission control; Resource allocation
- H04L47/72—Admission control; Resource allocation using reservation actions during connection setup
- H04L47/724—Admission control; Resource allocation using reservation actions during connection setup at intermediate nodes, e.g. resource reservation protocol [RSVP]
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/70—Admission control; Resource allocation
- H04L47/72—Admission control; Resource allocation using reservation actions during connection setup
- H04L47/726—Reserving resources in multiple paths to be used simultaneously
- H04L47/728—Reserving resources in multiple paths to be used simultaneously for backup paths
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/70—Admission control; Resource allocation
- H04L47/76—Admission control; Resource allocation using dynamic resource allocation, e.g. in-call renegotiation requested by the user or requested by the network in response to changing network conditions
- H04L47/765—Admission control; Resource allocation using dynamic resource allocation, e.g. in-call renegotiation requested by the user or requested by the network in response to changing network conditions triggered by the end-points
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/70—Admission control; Resource allocation
- H04L47/80—Actions related to the user profile or the type of traffic
- H04L47/801—Real time traffic
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/70—Admission control; Resource allocation
- H04L47/80—Actions related to the user profile or the type of traffic
- H04L47/805—QOS or priority aware
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/70—Admission control; Resource allocation
- H04L47/80—Actions related to the user profile or the type of traffic
- H04L47/808—User-type aware
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/70—Admission control; Resource allocation
- H04L47/82—Miscellaneous aspects
- H04L47/822—Collecting or measuring resource availability data
-
- H—ELECTRICITY
- H04—ELECTRIC COMMUNICATION TECHNIQUE
- H04L—TRANSMISSION OF DIGITAL INFORMATION, e.g. TELEGRAPHIC COMMUNICATION
- H04L47/00—Traffic control in data switching networks
- H04L47/70—Admission control; Resource allocation
- H04L47/82—Miscellaneous aspects
- H04L47/825—Involving tunnels, e.g. MPLS
Definitions
- This invention relates to a method and apparatus for allocating bandwidth during implementation of Quality of Service (QoS) using Internet Protocol (IP) provisioning. Specifically, the invention allocates bandwidth resources between service classes and during network congestion either buffers or randomly drops packets of lower quality of services to ensure delivery with minimized packet loss for higher quality of services.
- QoS Quality of Service
- IP Internet Protocol
- QoS Quality of Service
- data path mechanisms packet classification, policing, shaping, buffering, and scheduling
- control path mechanisms signalaling, resource reservation, routing
- the main concepts of diff-serv are: (1) aggregates of flows (rather than individual flows) receive a service; (2) the forwarding engine is required to provide delay and loss guarantees in a statistical or relative (rather than absolute quantitative) sense; and (3) the forwarding treatment that should be received by a packet is identified by a byte in the packet header, rather than by a flow lookup.
- the flow aggregates in diff-serv can be specified in several ways. To illustrate, consider a corporation that has three sites. Each site communicates with all the other sites over the Internet. A site may also communicate with other entities connected to the global Internet. In lo such a case, the flow aggregates that should receive differentiated QoS can be specified by:
- Point-to-point flows a set of packets originating from a first site and destined to a second site.
- Point-to-multi-point flows a set of packets originating from a first site and destined to either a second or a third site.
- Point-to-any-point flows any packet that originates from a first site and destined to any other site.
- RSVP Reserve Reservation
- QoS Quality of Service
- Internet Protocol supporting (1) a guarantee of performance under certain conditions, (2) supporting differentiation of product services with Internet providers, and (3) attaining economies of scale with multiple services integrated on a common network.
- the QoS should maximize the probability of delivery of packets for the highest levels of service while minimizing the probability of dropped packets. However, this optimization should not erode the lowest levels of service such that packet delivery delays for lower classes of services are so long that the lower classes of services cease to deliver the level of subscribed service.
- This invention is a diff-serv resource reservation system that checks to determine if sufficient bandwidth resources are available along the data flow pathway requested by the customer for a particular class of service.
- the resource reservation system determines the parameters such that a data packet can be transmitted according to the desired Quality of Service (QoS) parameters for the desired class.
- QoS Quality of Service
- a schedule optimizer ensures that sufficient buffer resource allocations and parameter settings in the routers and servers along the data path are made to optimally reach the predetermined QoS criteria for each of the desired classification of service levels.
- the system also contains a mechanism supporting resource reservation providing dynamic allocation of additional resources along alternative paths if the selected path links fail in the network.
- the resource management system optimizes packet traffic flow from (1) the values for the maximum QoS deterioration levels of the traffic caused by individual reservations for Virtual Leased Line traffic, (2) the maximum QoS deterioration levels of the Basic service caused by the Assured service, and (3) the packet loss ratios of the Assured versus the Basic services. These values provide information necessary for determining capacity planning and provide the minimum utilization of a link to be considered when congestion occurs. Average utilization of Virtual Leased Line traffic with respect to the peak rate subscribed along each link is computed versus the maximum percentage of the total Virtual Leased Line subscription with respect to the link capacity. Preconfiguration of all the routers with parameter settings for Weighted Fair Queuing (WFQ), buffer allocations, and Weighted Random Early Discard (WRED) further allows the resource reservation system to maintain the desired QoS in the network.
- WFQ Weighted Fair Queuing
- WRED Weighted Random Early Discard
- FIG. 1 illustrates the hierarchy of service classifications according to Virtual Leased Line, Assured and Basic service classes in a fixed bandwidth environment.
- FIG. 2 illustrates the routing scheme of a typical path for data or voice over a series of routers.
- FIG. 3 illustrates the Virtual Leased Line origin shaping the traffic for the Virtual Leased Line service.
- FIG. 4 illustrates a flow chart describing the configuration of the router parameters.
- FIG. 5 illustrates a flow chart describing the buffering scheme for Virtual Leased Line, Assured and Basic traffic.
- FIG. 6 illustrates a chart describing the packet drop probability for Weighted Random Early Discard (WRED) as a function of average queue size.
- WRED Weighted Random Early Discard
- FIG. 7 illustrates when WRED is used to differentiate the QoS for Assured and Basic services, and the probability of dropping Basic packets is more probable than the probability of dropping Assured Packets.
- FIG. 8 illustrates a flow chart describing the Assured service setting of the rate of traffic flow and warning flags.
- FIG. 9 illustrates a flow chart describing the Assured service setting of the rate of traffic flow and warning flags.
- FIG. 10 illustrates a flow chart describing the Assured service setting of the rate of traffic flow and warning flags.
- FIG. 1 illustrates the three classes of services: Virtual Leased Line ( 10 ), Assured ( 12 ) and Basic ( 14 ) services supported across a data line of fixed bandwidth ( 15 ) for Quality of Service (QoS) functionality. These three classes of services have different characteristics in order to satisfy the service demands of a user.
- Virtual Leased Line service ( 10 ) is designed for applications and customers that require predictable point-to-point performance.
- a Virtual Leased Line ( 10 ) is a point-to-point data line with a guaranteed peak transmission rate. Implementing performance restrictions and setting criteria on the line, packet loss due to network congestion, delay, and delay-jitter is minimized. Examples of applications employing Virtual Leased Line level of service ( 10 ) include Voice over Internet Protocol (VoIP), transaction processing, and multimedia applications that require low delay and jitter.
- VoIP Voice over Internet Protocol
- the second class of service in the hierarchy is;Assured service ( 12 ) and is designed for customers who need “better than best-effort service.” When congestion exists, packets that receive Assured service ( 12 ) gain a degree of priority over packets that receive Basic service ( 14 ) in terms of packet loss.
- Basic service ( 14 ) the lowest class of service, is designed for customers who require general Internet access where some delay is not critical to the success of the application.
- Basic service ( 14 ) is the equivalent of best-effort delivery service that is widely used in current Internet servicing.
- a Virtual Leased Line ( 10 ) can be realized independently of Assured service, and vice versa.
- the three-class model can be extended with more classes to include additional enhanced classes that are similar to the Virtual Leased Line service ( 10 ) class but also provide for over-booking of packets and thus can be subscribed to by a customer at a less expensive rate.
- a Virtual Leased Line ( 10 ) transmitting packets is not over-booked.
- the remaining bandwidth ( 16 ) is available to Assured ( 12 ) and Basic ( 14 ) traffic flows. That is, Assured ( 12 ) and Basic ( 14 ) traffic flows share the bandwidth not committed to Virtual Leased Line ( 10 ) traffic flows as well as any idle bandwidth committed to Virtual Leased Line ( 10 ) traffic flows.
- Assured ( 12 ) traffic flows obtain a degree of protection against overloads of Basic ( 14 ) traffic. Assured ( 12 ) packets get priority over Basic ( 14 ) packets at each hop, but unlike the case for Virtual Leased Line ( 10 ) packets, the routers provide no guarantee that the delays at all hops along the flow path will be small. Instead, traffic measurement, provisioning systems plans and management of the network capacity allow Assured ( 12 ) traffic flows to experience small delays with sufficiently high probability. With appropriate traffic engineering and pricing, Assured ( 12 ) traffic consistently sees a lightly loaded “best-effort” 0 network.
- traffic capacity on a particular link is shared among Virtual Leased Line ( 10 ), Assured ( 12 ), and Basic ( 14 ) traffic services.
- Virtual Leased Line ( 10 ) traffic obtains the highest priority, but is limited by a traffic rate cap ( 18 ).
- Virtual Leased Line ( 10 ) capacity ( 16 ) can be utilized by Assured ( 12 ) and Basic ( 14 ) packets.
- One mechanism for optimizing traffic flow supports a prioritized dropping of some of the packets differentiating Assured ( 12 ) traffic flow from Basic ( 14 ) traffic flow.
- the three classes of service operate using a traffic priority scheme configured such that priority is given to Virtual Leased Line ( 10 ) traffic such that the service quality to the Assured ( 12 ) and Basic ( 14 ) classes is impacted.
- the priority scheme for the Assured ( 12 ) service class impacts the quality of service to the Basic ( 14 ) service class.
- weight assignments employed in a Weighted Fair Queuing (WFQ) packet scheduling mechanism could employ variations of weighted round-robin schemes such as Modified Deficit Round Robin “M-DRR” 0 as an approximation of WFQ when the number of queues is small;
- WFQ Weighted Fair Queuing
- Virtual Leased Line service ( 10 ) guarantees a unidirectional reserved rate R f for a point-to-point flow. When packets arrive at an ingress point in the network at a rate exceeding R f , they are dropped prior to entering the network.
- the reserved rate supported by the Virtual Leased Line service ( 10 ) may be renegotiated or may vary over time.
- Virtual Leased Line service ( 10 ) is similar to leased line service, but a leased line service guarantees a fixed delay, while the delay in Virtual Leased Line service ( 10 ) is variable but typically very low.
- the Virtual Leased Line service ( 10 ) is typically realized on an Internet Protocol network that statistically multiplexes its resources among several services across a virtual circuit.
- the time-scale at which the transmission rate can be changed is smaller for a Virtual Leased Line ( 10 ) service than a leased line service.
- FIG. 2 illustrates the routing scheme of a typical path for data or voice over a series of nodes.
- the path of a first Virtual Leased Line ( 20 ) across voice gateways 1 ( 22 ) and 3 ( 24 ) traverses nodes R 2 ( 26 ), R 5 ( 28 ) and R 4 ( 30 ), respectively.
- R 2 ( 26 ), R 5 ( 28 ) and R 4 ( 30 ) are routers but other communication devices can also be utilized to receive and transmit packets along the communication network.
- the path of a second Virtual Leased Line ( 32 ), across voice gateways 1 ( 22 ) and 2 ( 34 ) traverses the same routed path except the path between nodes R 4 ( 30 ) and voice gateway 2 ( 34 ).
- the bandwidth requests of the first ( 20 ) and second ( 32 ) Virtual Leased Lines are reserved individually on the nodes R 2 ( 26 )-R 5 ( 28 ) and R 5 ( 28 )-R 4 ( 30 ) links, and the nodes R 2 ( 26 )-R 5 ( 28 ), and R 5 ( 28 )-R 4 ( 30 ), respectively.
- the nodes R 2 ( 26 )-R 5 ( 28 ), and R 5 ( 28 )-R 4 ( 30 ) are router
- Each of the nodes or routers along the path for the first ( 20 ) and the second ( 32 ) Virtual Leased Lines must reserve a sufficient bandwidth for the packet traffic resources for both the Virtual Leased Lines ( 20 ) and ( 32 ) operating at peak performance. Additional nodes or routers RI ( 36 ), R 3 ( 38 ) and R 6 ( 40 ) can be connected to the other nodes or routers on the network handling the first Virtual Leased Line ( 20 ) and the second Virtual Leased Line ( 32 ). Allocation of the bandwidth along secondary routes also needs to be calculated to support Virtual Leased Line services along the primary pathways.
- the voice gateways 1 ( 22 ), 2 ( 34 ) and 3 ( 24 ) comprise systems that are typically computers, routers or information appliances that typically include a microprocessor ( 42 ), memory system ( 44 ), and a communication interface or connection ( 46 ) that allows the system and voice gateway to be connected to the communication network.
- Other components comprising the system are a packet transmission delivery device ( 48 ), a communication network sensing mechanism ( 50 ), a controller ( 51 ), a bandwidth allocation device ( 52 ), and a memory buffer ( 54 ).
- the communication interface or connection ( 46 ) may be a modem or other data packet transmission and receiving device.
- the communication sensing mechanism ( 50 ) is capable of sensing the topology of the communication network including the network's router parameters and characteristics.
- the controller ( 51 ) is capable of scheduling the transmission of the packets across the communication network.
- the bandwidth allocation device ( 52 ) is capable of allocating and reserving sufficient bandwidth according to a preselected scheme corresponding to service classifications.
- the memory buffer ( 54 ) allows the system to buffer certain service classification packets to maximize the probability of packet delivery for higher classes of packet delivery services.
- the architecture will redirect packet traffic along alternative routes.
- a calculation is made along alternative pathways such as the data pathway on nodes R 2 ( 26 )-R 1 ( 36 )-R 3 ( 38 )-R 4 ( 30 ).
- node R 5 ( 28 ) fails, the architecture automatically redirects the packet traffic along the alternative pathway because the architecture has reserved Virtual Leased Line bandwidth along the alternative pathways.
- the links between nodes R 4 ( 30 )-R 5 ( 28 ) and R 5 ( 28 )-R 2 ( 26 ) must be able to serve all Virtual Leased Line service links in the route.
- the summation of all the reserved rates or guaranteed bandwidth for Virtual Leased Lines on a particular link must be less than the total bandwidth allocation for Virtual Leased Line class on that link. Guarantees for no packet loss for Virtual Leased Line service can be made only if the aggregate rate reserved for all the Virtual Leased Lines services on any link is less than the total capacity available on that link.
- the bandwidth share that can safely be dedicated to Virtual Leased Line service without adverse impact on Assured and Basic classes requires setting some predetermined criteria and parameters.
- Various levels of service availability can be provided on links based on the time scale corresponding to recover time from a link or router failure. Given enhanced forwarding and routing capabilities typical of most routers, such as those available in Multi-Protocol Layered Switching (MPLS), recovery times can be reduced to the millisecond range. If the Virtual Leased Line service guarantees are to be maintained during a router failure, then Virtual Leased Line capacity planning and admission control has to account for the alternative paths that must be reserved for different failure scenarios. However, accounting for these alternative paths may limit the total amount of Virtual Leased Line traffic admitted along the various links.
- MPLS Multi-Protocol Layered Switching
- FIG. 3 illustrates the Virtual Leased Line: origin shaping the traffic for the Virtual Leased Line service.
- the packets are marked according to the Virtual Leased Line service class ( 300 ). If the origin node cannot be trusted to shape the packets appropriately ( 304 ), then the policing is carried out at the trust boundary ( 306 ). This is accomplished by implementing the appropriate setting of the Internet Protocol precedence bits of the packet ( 308 ). In particular, using the router's policing mechanism, the ingress router can drop packets arriving at a rate exceeding the reserved rate.
- the router identifies the packets belonging to the Virtual Leased Line service class-based on the Diffserv Codepoints (DSCP) in the packet's header.
- the expedited packet handling behavior denotes the Virtual Leased Line service class.
- the router To access the Virtual Leased Line service, the router makes the following two scheduling decisions:
- the allocation of link bandwidth ( 310 ) between the Virtual Leased Line and other service classes provides extremely low delay and jitter to the Virtual Leased Line service class; the router is programmed to prioritize the scheduling.
- the router may employ a class-based scheduling algorithm ( 314 ) that allocates bandwidth among various service classes in a weighted fair manner ( 316 ), such as by WFQ or M-DRR.
- the router may have to emulate priority behavior by assigning a sufficiently large weight to the Virtual Leased Line class. This weight provision may be required to be significantly larger than what is typically necessary to allocate the desired bandwidth to the appropriate class. For example, if 20% bandwidth is allocated to Virtual Leased Line, a network administrator may have to assign a weight that allocates 50% bandwidth.
- the router could employ a single first-in, first-out (FIFO) relationship scheme is ( 318 ) for these traffic flows.
- FIFO first-in, first-out
- VoIP Voice-over-IP
- Virtual Leased Line service typically guarantees a near-zero packet loss due to congestion. This guarantee can typically only be made if the aggregate rate reserved for all the Virtual Leased Lines on any link is less than the capacity available on that link for the Virtual Leased Line service. To ensure that this condition is met, a Bandwidth Broker network management tool can be used. As Multi-Protocol Layered Switching (MPLS) mechanisms become available, they also can be used to provide enhanced control of the Virtual Leased Line path and to provide ultra-fast restoration capabilities in response to router failures. RSVP, as a signaling protocol for aggregate QoS flows, can also improve the flexibility of QoS subscriptions by changing the signaling protocol from a current static subscription to a dynamic subscription in both time-scale and rate renegotiations.
- MPLS Multi-Protocol Layered Switching
- a Bandwidth Broker tool can be used to help achieve the setting of these parameters for routers located along the data pathway between the ingress and egress points of the network. For example, when a customer wants to subscribe to a Virtual Leased Line path from point A to point B, the Bandwidth Broker tool can apply an inter-domain routing protocol such as Open Shortest Path First (OSPF) to find the exact series of links the Virtual Leased Line path will traverse. The Bandwidth Broker tool also determines if each of these links has a sufficient bandwidth to support the Virtual Leased Line subscription. If there is a sufficient bandwidth, the subscription is accepted; otherwise, the required Virtual Leased Line rate cannot be honored.
- OSPF Open Shortest Path First
- FIG. 4 illustrates a flow chart describing the configuration of the router parameters.
- Router parameters are determined based on the three classes of services between a particular link.
- packets are treated as the Basic traffic ( 400 ).
- Part of overall traffic flow is classified as Virtual Leased Line traffic ( 402 ) while the remaining traffic continues to be treated as Basic traffic.
- Virtual Leased Line traffic 402
- additional packets are selected and classified as Assured traffic ( 404 ).
- the following design criteria ( 406 ) for the router parameters is set to achieve:
- TCP transmission control protocol
- Virtual Leased Line traffic is designed such that the QoS of service for the Assured and Basic traffic flows does not experience significant deterioration.
- the time average packet loss ratio is used at each outgoing link as a measure of QoS of the three classes. If P V , P A , and P B denote the long time average packet loss ratios ( 408 ) of the Virtual Leased Line, Assured, and Basic traffic, then P all denotes the long time average packet loss ratio of all traffic. If P all ⁇ V denotes the long time average packet loss ratio of the combined Assured and Basic traffic, then both classes are treated as lesser quality of services and the Virtual Leased Line service receives premium status.
- Traffic engineering considerations for Assured services provide the desired traffic ratio ( 414 ) between the Assured and Basic services. Enforcement of such a ratio is difficult for all links for given values of ⁇ A and ⁇ A .
- the optimal solution is to monitor this traffic ratio ( 414 ) for all links and only take action when the total utilization of the link is greater than 80% and the Assured and Basic traffic ratio ( 414 ) is more than the desired value obtain from the equation above. If this scenario occurs, application of Multi-Protocol Layered Switching (MPLS), explicit routing technology or obtaining an additional bandwidth for the link are possible solutions.
- MPLS Multi-Protocol Layered Switching
- the primary QoS requirements ( 416 ) for the Virtual Leased Line having zero packet loss during congestion, low queuing delay and jitter can be realized through implementation of: (1) admission control ( 418 ) of the total peak Virtual Leased Line traffic to any interface, (2) appropriate assignment of weights ( 420 ) in WFQ, and (3) appropriate buffer allocation ( 422 ).
- the Bandwidth Broker tool can be utilized to track the Bandwidths of the various links. CAR is used at ingress routers to drop any Virtual Leased Line packets above the subscribed rate of the customer.
- Weights ( 420 ) for Virtual Leased Line service WFQ are ideally 100% for the minimize cross-class jitter for Virtual Leased Line. However, assigning a value of 100% may cause starving for the remaining traffic when the bulk of the Virtual Leased Line packets arrive at the queue in short time intervals or when admission control on Virtual Leased Line traffic fails in some ingress points of the network, causing non-Virtual Leased Line traffic to be marked as Virtual Leased Line Traffic.
- the value of w V can be adjusted to higher values on some AR links where the majority of the traffic is for Virtual Leased Line service.
- the minimum buffer size ( 422 ) for controlling packet loss on the Virtual Leased Line is derived from the minimum buffer space that is available for the Virtual Leased Line traffic. Determining the minimum buffer size ( 422 ) typically ignores the intermediate hops that the Virtual Leased Line traffic traverse before reaching the considered out-going link interfaces. Since almost all Virtual Leased Line traffic comes from different customer routers, independence among Virtual Leased Line traffic is assumed. In addition, a Virtual Leased Line subscription is upper-bounded by its peak rates and the sum of all the peak rates has to be less than 50% of the link capacity. The router parameters are then configured ( 424 ) for the transmission of the traffic on the network.
- this system can be described as N independent Virtual Leased Lines always running at their peak rates where N is the total number of Virtual Leased Lines.
- the queuing scheme that is used is typically denoted as N*D/D/1.
- M/D1 model can also be used to replace the N*D/D/1 model. This simplifies the computations while the queue length estimated is normally greater than the one using N*D/D/1 modeling.
- the asymptotic result of M/D/1 modeling is applied:
- B V - ⁇ ln ⁇ ⁇ p 2 ⁇ ( 1 - ⁇ )
- An estimate of the maximum delay at a router for an outgoing link of an Optical Carrier Level 3 (OC 3 ) link when the packet size is 1500 bytes, is a maximum of 0.155 ms to transmit one packet when 50% of the OC 3 bandwidth is reserved for Virtual Leased Line traffic. Based on the computation above, there is less than 10 ⁇ 6 probability that a Virtual Leased Line packet will be subject to 10.6 ms delay at an OC 3 interface link. If the VoIP packet size is reduced in size to 120 bytes, the 10.6 ms delay is further reduced to 0.85 ms for the transmission of an Ethernet packet.
- VoIP encapsulation comprises 40 bytes (20 bytes for the Internet Protocol header, 8 bytes for the User Datagram Protocol (UDP) header, and 12 bytes for Real Time Protocol (RTP)).
- UDP User Datagram Protocol
- RTP Real Time Protocol
- DS 3 Digital Signal, Level 3
- the buffer management scheme shares buffer space by allocating and separating the packets according to the classes of service. A global threshold is determined for all queues and a series of local thresholds are determined for each queue. For the three classes of services, Virtual Leased Line, Assured and Basic, only two buffers are required: one for the Virtual Leased Line traffic and one for the Assured traffic. Additional buffers would be used if additional service classes were implemented.
- FIG. 5 illustrates a flow chart describing the buffering scheme for Virtual Leased Line, Assured and Basic traffic.
- a packet arrives ( 500 )
- a determination is made to ascertain ( 502 ) whether the instantaneous queue length for all the classes is less than the maximum buffer size of the queue. If the determination is affirmative, the packet is dropped ( 504 ). If not, the buffering scheme determines if the packet belongs to a particular queue i ( 506 ). Next, the buffering scheme determines whether the instantaneous queue length for all classes is greater than the global threshold ( 508 ). If the global threshold is not exceeded, the packet is admitted to the queue i ( 510 ).
- the two queues can buffer more packets than the limitations implemented by the local thresholds. If the global threshold is exceeded, then the buffering scheme determines if the instantaneous queue length of the queue i is greater than the local threshold for queue i ( 512 ). If the local threshold is exceeded, then the packet is dropped ( 514 ). Otherwise, the buffering scheme determines whether the packet can be randomly dropped using WRED ( 516 ). The packet is dropped ( 514 ) if the analysis using WRED is met. Otherwise, the packet is admitted to queue i ( 510 ). However, packets that are already in the queue are not discarded, even if the queue exceeds the individual limit for that class of service.
- the primary function of the buffer is to absorb the bursts of packet traffic and therefore increase the utilization of the transmission router. If G denotes the global threshold, L V denotes the local thresholds for the Virtual Leased Line traffic, and L A+B for the Assured and Basic traffic combined, then:
- B is the maximum buffer size.
- the maximum buffer size is typically determined based on the desired maximum delay for any given link rate. Otherwise, some buffer space B ⁇ (L V +L A+B ) may be wasted when the combined queue has reached the global threshold and the local thresholds.
- the local threshold is designed to ensure the designated traffic has a certain degree of guarantee of access to the buffer.
- the local threshold implies that L V +L A+B >B; otherwise, when the sum of Assured and Basic packets reach L A+B , the Virtual Leased Line packets may not have full access to the local buffer space L V .
- the global threshold is designed to support buffer sharing so that utilization of the transmission router can be optimized. Therefore, from a utilization perspective, the larger values of G support increased utilization. However, when only two queues exist, a primary concern is guaranteeing the minimum buffer size B V for the Virtual Leased Line traffic. Therefore:
- V max an upper bound on the maximum buffer size for the Virtual Leased Line queue
- the number of the Virtual Leased Line packets in the queue is usually less than G. This provides that the Virtual Leased Line packets are almost guaranteed a minimum buffer space B V and guarantees the Virtual Leased Line packet loss probability to be at most p. This also allows the majority of the buffer space to be used for the Assured and Basic packets.
- Random Early Detection as a congestion avoidance mechanism to improve TCP throughput and fairness while reducing average packet loss allows the current average queue size to be congested by:
- the dropping probability on the incoming packet is determined based on three related parameters: (1) the minimum threshold min th value, (2) the maximum threshold max th value, and (3) the probability denominator den.
- RED starts randomly dropping incoming packets.
- the probability of random packet dropping increases linearly as the average queue size increases until the average queue size reaches the maximum threshold.
- the inverse of the probability denominator is the fraction of packets dropped when the average queue depth is at the maximum threshold, denoted as P max . For example, if the denominator, den, is (512), one out of every (512) packets is dropped when the average queue is at the maximum threshold. When the average queue size is above the maximum threshold, all packets are dropped.
- FIG. 6 illustrates the packet drop probability for Random Early Detection (RED) as a function of average queue size ( 600 ).
- RED Random Early Detection
- the computed average queue size ( 600 ) is always less than or equal to the total buffer size max th ( 602 ).
- max th the total buffer size
- packets are randomly dropped. As the number of packets in the queue increases beyond the minimum point min th ( 604 ), the number of dropped packets increases until the maximum buffer limit max th ( 602 ) is reached.
- probability of dropping packets P b ( 606 ) reaches a maximum point P max ( 608 ), and all packets are dropped ( 610 ).
- This rate of dropped packets can be achieved by adjusting the dropping probability according to the number of undiscarded packets that have arrived since the last discarded packet, denoted as count.
- FIG. 7 illustrates when WRED is used to differentiate the QoS for Assured and Basic services, and the probability of dropping Basic packets is more probable than the probability of dropping Assured packets.
- Assured services can achieve better performance deliveries than Basic service, when the average queue size is computed based on the aggregate queue size ( 700 ).
- the goal is to select a set of min th ( 702 ), max th ( 704 ), and P max ( 706 ) and ( 708 ) for each of the Assured and Basic service classes. These values are based on values obtained from P A /P B ⁇ A where P A and P B are packet loss ratios of the Assured and Basic services, respectively.
- the computed average queue size ( 700 ) is less than or equal to the total buffer size.
- max th ( 704 ) of the Assured service and max th ( 704 ) of the Basic service select the same value for max th ( 704 ) of the Assured service and max th ( 704 ) of the Basic service.
- TCP connection throughput constant average packet loss ratio Assured TCP throughput Basic TCP throughput ⁇ 1 ⁇ A
- a computer or server connected to a network of other servers or computers provides the hardware for implementing the Bandwidth Broker aspects of this invention.
- the computer is connected to the network by a modem or other interface allowing for the transmission and reception of data over a network such as the Internet or an Intranet.
- One or more microprocessors in the computer receives commands that select data and organize the data for lo transmission in packets across the network. Additional commands received and executed by the computer's processors or network sensing mechanism allow the computer to sense the topology and routing parameters of the network. Other commands received and executed by the computer's processors or packet transmission delivery mechanism support the classification of the data packets according to a prespecified service class level. In a typical example, the prespecified service class levels would be Virtual Leased Line, Assured and Basic service classes.
- Additional sensing performed by the computer supports the selection of a primary and alternate or secondary pathways for transmitting the data packets from a starting point to a destination point.
- the computer can ascertain whether a request to transmit data packets across the network along a particular pathway can be processed based on the available bandwidth remaining for the selected service class level. If available bandwidth exists, the data packet can receive a reservation on the pathway with a guarantee of required bandwidth to ensure proper delivery of the data packet.
- the computer can facilitate the changing of router or other parameters involved in transmitting data packets, i.e., bandwidths for the different levels of service classifications can be modified and changed based on the requirements of the customer.
- the Bandwidth Broker's major functionality includes provisioning Virtual Leased Line subscriptions, provisioning Assured subscriptions, and traffic monitoring.
- the subscriptions granted can be made by static or dynamic decisions.
- Static Virtual Leased Line service provisioning occurs when a prospective Virtual Leased Line customer submits a purchase request for Virtual Leased Line service. A determination is made whether the request can be categorized into one or multiple point-to-point, unidirectional Virtual Leased Lines. For each Virtual Leased Line, the customer should provide the Internet Protocol addresses of the two end points and the peak rate of the Virtual Leased Line service to be subscribed.
- the Bandwidth Broker determines if the request can be accepted or denied based on the available bandwidth along each link in the required path. The steps for making this decision are as follows:
- the Bandwidth Broker should maintain the updated information on the network topology, the Open Shortest Path First (OSPF) metric assigned to all links, line speeds of all links, the maximum bandwidth that can be subscribed to the Virtual Leased Line service for each link, all Virtual Leased Line routes and rates currently subscribed to customers, and the bandwidth already subscribed to Virtual Leased Line service of each link under the normal condition.
- OSPF Open Shortest Path First
- FIG. 8 illustrates a flow chart describing the Virtual Leased Line service setting of the rate of traffic flow and warning flags.
- the Bandwidth Broker determines ( 802 ) whether the topology or OSPF metric has changed. If a change has not occurred, the analysis ends ( 804 ). If a change has occurred, the Bandwidth Broker determines if a new path is being established ( 806 ). If a new path is not being established, the analysis ends ( 804 ). Otherwise, the Bandwidth Broker determines the load balancing policy of the router ( 808 ). Next, the Bandwidth Broker determines ( 810 ) the traversing paths for each pair of ingress and egress routers on the network.
- the Bandwidth Broker determines and tracks the total peak rate of the Virtual Leased Line subscribed along each link of the network ( 812 ). The maximum bandwidths are input for subscription relative to the total Virtual Leased Line peak rate for each link in the network ( 814 ). Then the Bandwidth Broker determines the traversing path when a Virtual Leased Line subscription request is received at the ingress router ( 816 ). Connection A ( 818 ) links FIG. 8 and FIG. 9 .
- the Bandwidth Broker determines whether the Virtual Leased Line traffic along every link can accommodate the Virtual Leased Line service ( 820 ). If the Virtual Leased Line service cannot be accommodated, then the Virtual Leased Line request is denied ( 822 ). If the request is granted, the Bandwidth Broker determines whether for every failed path, an alternative path can be established to accommodate the requested Virtual Leased line rate ( 824 ). If the Virtual Leased Line service can not be accommodated, then the Virtual Leased Line request is denied ( 822 ). If the request is granted, the Bandwidth Broker accepts the Virtual Leased Line request ( 826 ), updates the total subscribed Virtual Leased Line rates ( 828 ), and sets the warning flags ( 830 ).
- Routing protocols such as OSPF always select the shortest path for packet forwarding.
- the OSPF cost metric assigned to all links is independent of real-time traffic through the links and the shortest path will remain unchanged as long as the network topology and metric assigned to all links remain unchanged.
- FIG. 10 illustrates a flow chart describing the Assured service setting of the rate of traffic flow and warning flags.
- Assured service provisioning when a prospective Assured customer submits a purchase request for Assured service, the rate is also specified.
- the Bandwidth Broker determines if the request can be accepted or denied. This decision is based on the total Assured traffic that should be admitted into the backbone.
- the Bandwidth Broker determines the Assured rate requested by the prospective customer ( 1002 ). The Bandwidth Broker also determines the maximum total rate that can be allowed for the Assured service at the requested Assured rate ( 1004 ). The remaining rate for the Assured service is then calculated for other Assured rates.
- the Bandwidth Broker compares the requested Assured rate with the remaining Assured service rate availability ( 1006 ). The rate request is denied if the remaining rate is smaller than the required rate ( 1008 ), otherwise the Assured rate request is accepted ( 1010 ). If the Assured rate request is accepted ( 1010 ), the remaining available Assured rates are updated in the router databases ( 1012 ) as well as the customer data.
- the Bandwidth Broker continues to monitor the traffic ratio of Assured service versus the Basic service for each link ( 1014 ). By performing this monitoring, warning flags ( 1016 ) are set for those links with ratios above a pre-specified threshold. This requires that the Bandwidth Broker monitor the network traffic for Assured and Basic service classes for a pre-specified time interval. In addition, the Bandwidth Broker should monitor the remaining Virtual Leased Line bandwidth on each link. Warning flags are also set for those links to alert the network when the Virtual Leased Line bandwidth exceeds a pre-specified threshold.
- the Bandwidth Broker can be extended to support a dynamic subscription.
- the Bandwidth Broker serves as a part of the provisioning and monitoring tool for differentiated classes of services.
- the Bandwidth Broker can be integrated with a policy server where QoS policies are enforced and can become a part of the Policy Decision Point (PDP) where decisions are made according to the policies.
- PDP Policy Decision Point
- the decisions are realized at the Policy Enforcement Points (PEPs), i.e., the associated network devices (router, gateway, firewall, etc.).
- PEPs Policy Enforcement Points
Abstract
Description
| Desired Throughput Ratio | 1.5 | 2 | 2.5 | 3 | ||
| of A vs. B | ||||||
| αA Needed | 0.444 | 0.250 | 0.160 | 0.111 | ||
Claims (21)
Priority Applications (2)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US09/475,512 US6744767B1 (en) | 1999-12-30 | 1999-12-30 | Method and apparatus for provisioning and monitoring internet protocol quality of service |
| US10/806,742 US6973033B1 (en) | 1999-12-30 | 2004-03-23 | Method and apparatus for provisioning and monitoring internet protocol quality of service |
Applications Claiming Priority (1)
| Application Number | Priority Date | Filing Date | Title |
|---|---|---|---|
| US09/475,512 US6744767B1 (en) | 1999-12-30 | 1999-12-30 | Method and apparatus for provisioning and monitoring internet protocol quality of service |
Related Child Applications (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US10/806,742 Continuation US6973033B1 (en) | 1999-12-30 | 2004-03-23 | Method and apparatus for provisioning and monitoring internet protocol quality of service |
Publications (1)
| Publication Number | Publication Date |
|---|---|
| US6744767B1 true US6744767B1 (en) | 2004-06-01 |
Family
ID=32326761
Family Applications (2)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US09/475,512 Expired - Fee Related US6744767B1 (en) | 1999-12-30 | 1999-12-30 | Method and apparatus for provisioning and monitoring internet protocol quality of service |
| US10/806,742 Expired - Fee Related US6973033B1 (en) | 1999-12-30 | 2004-03-23 | Method and apparatus for provisioning and monitoring internet protocol quality of service |
Family Applications After (1)
| Application Number | Title | Priority Date | Filing Date |
|---|---|---|---|
| US10/806,742 Expired - Fee Related US6973033B1 (en) | 1999-12-30 | 2004-03-23 | Method and apparatus for provisioning and monitoring internet protocol quality of service |
Country Status (1)
| Country | Link |
|---|---|
| US (2) | US6744767B1 (en) |
Cited By (102)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US20010019554A1 (en) * | 2000-03-06 | 2001-09-06 | Yuji Nomura | Label switch network system |
| US20010023443A1 (en) * | 2000-03-20 | 2001-09-20 | International Business Machines Corporation | System and method for reserving a virtual connection in an IP network |
| US20010027484A1 (en) * | 2000-03-30 | 2001-10-04 | Nec Corporation | Quality assured network service provision system compatible with a multi-domain network and service provision method and service broker device |
| US20010051992A1 (en) * | 2000-02-24 | 2001-12-13 | Brian Yang | Unified algorithm for frame scheduling and buffer management in differentiated services networks |
| US20020059427A1 (en) * | 2000-07-07 | 2002-05-16 | Hitachi, Ltd. | Apparatus and method for dynamically allocating computer resources based on service contract with user |
| US20020075863A1 (en) * | 2000-12-20 | 2002-06-20 | Yoshimi Nakagawa | Pathsize control method and operation of transmission apparatus |
| US20020091804A1 (en) * | 2000-11-06 | 2002-07-11 | Ward Julie Ann | Reliability for interconnect fabrics |
| US20020093925A1 (en) * | 2001-01-18 | 2002-07-18 | Chuah Mooi Choo | Universal mobile telecommunications system (UMTS) quality of service (QoS) supporting variable QoS negotiation |
| US20020118646A1 (en) * | 2000-12-21 | 2002-08-29 | Jean-Francois Saint Etienne | Device and process for flow control in a switched network |
| US20020124091A1 (en) * | 2001-03-01 | 2002-09-05 | Yoshitoshi Kurose | Network service setting system, network service providing method and communication service |
| US20020126579A1 (en) * | 1999-09-20 | 2002-09-12 | Gualtieri Devlin M. | Steered beam ultraonic sensor for object location and classification |
| US20020145982A1 (en) * | 2000-11-03 | 2002-10-10 | Talpade Rajesh Rasik | Method and system for quality of service provisioning for IP virtual private networks |
| US20020181401A1 (en) * | 2001-05-30 | 2002-12-05 | Hassan Hagirahim | Method of providing quality of service (QOS) to voice applications in routed IP networks |
| US20020188648A1 (en) * | 2001-05-08 | 2002-12-12 | James Aweya | Active queue management with flow proportional buffering |
| US20030028641A1 (en) * | 2001-07-30 | 2003-02-06 | Zhi-Li Zhang | Method and apparatus for a bandwidth broker in a packet network |
| US20030043740A1 (en) * | 2001-06-14 | 2003-03-06 | March Sean W. | Protecting a network from unauthorized access |
| US20030084144A1 (en) * | 2001-10-30 | 2003-05-01 | Lipinski Greg J. | Network bandwidth optimization method and system |
| US20030144822A1 (en) * | 2002-01-31 | 2003-07-31 | Li-Shiuan Peh | Generating interconnect fabric requirements |
| US20030148768A1 (en) * | 2002-02-01 | 2003-08-07 | Naveen Kakani | Method and system for service rate allocation, traffic learning process, and QoS provisioning measurement of traffic flows |
| US20030195919A1 (en) * | 2002-03-26 | 2003-10-16 | Tatsuya Watanuki | Packet distributing system and method for distributing access packets to a plurality of server apparatuses |
| US20040078733A1 (en) * | 2000-07-13 | 2004-04-22 | Lewis Lundy M. | Method and apparatus for monitoring and maintaining user-perceived quality of service in a communications network |
| US20040090914A1 (en) * | 2001-03-07 | 2004-05-13 | Briscoe Robert J | Communications network |
| US20040095887A1 (en) * | 2000-01-18 | 2004-05-20 | At&T Corp. | Apparatus and method for designing a network |
| US20040100908A1 (en) * | 2002-11-27 | 2004-05-27 | Khosravi Hormuzd M. | Method and apparatus to provide IP QoS in a router having a non-monolithic design |
| US20040109414A1 (en) * | 2002-12-10 | 2004-06-10 | Choi Gil Young | Method of providing differentiated service based quality of service to voice over internet protocol packets on router |
| US20040117426A1 (en) * | 2001-04-19 | 2004-06-17 | Steven Rudkin | Communications network |
| US20040172464A1 (en) * | 2000-07-28 | 2004-09-02 | Siddhartha Nag | End-to-end service quality for latency-intensive internet protocol (IP) applications in a heterogeneous, multi-vendor environment |
| US20040196855A1 (en) * | 2000-10-03 | 2004-10-07 | U4Ea Technologies Limited | Prioritizing data with flow control |
| US20040205762A1 (en) * | 2003-02-24 | 2004-10-14 | Kabushiki Kaisha Toshiba | Communication control apparatus, communication control method and communication control program product |
| US20040218607A1 (en) * | 2003-04-30 | 2004-11-04 | Tuija Hurtta | Handling traffic flows in a mobile communications network |
| US20040223456A1 (en) * | 2001-03-06 | 2004-11-11 | Deepak Mansharamani | System for fabric packet Control |
| US20050044263A1 (en) * | 2001-05-08 | 2005-02-24 | Wei Zhang | Scheduling method of realizing the quality of service of router in integrated service |
| US20050089042A1 (en) * | 2003-10-24 | 2005-04-28 | Jussi Ruutu | System and method for facilitating flexible quality of service |
| US20050135375A1 (en) * | 2003-12-19 | 2005-06-23 | Nokia Corporation | Control decisions in a communication system |
| WO2005081474A1 (en) * | 2004-02-25 | 2005-09-01 | National University Of Singapore | Qos in optical networks |
| US6959335B1 (en) * | 1999-12-22 | 2005-10-25 | Nortel Networks Limited | Method of provisioning a route in a connectionless communications network such that a guaranteed quality of service is provided |
| US6961307B1 (en) * | 1999-12-06 | 2005-11-01 | Nortel Networks Limited | Queue management mechanism for proportional loss rate differentiation |
| US20050265359A1 (en) * | 2004-05-13 | 2005-12-01 | Drew Julie W | Optimizing switch port assignments |
| US6973315B1 (en) * | 2001-07-02 | 2005-12-06 | Cisco Technology, Inc. | Method and system for sharing over-allocated bandwidth between different classes of service in a wireless network |
| US6977905B1 (en) | 2001-06-01 | 2005-12-20 | Cisco Technology, Inc. | Network with self regulating quality of service (QoS) |
| US6996062B1 (en) * | 2001-02-28 | 2006-02-07 | 3Com Corporation | Policy-based weighted random early detection method for avoiding congestion in internet traffic |
| US7015949B1 (en) | 2001-04-12 | 2006-03-21 | Ipix Corporation | Method and apparatus for hosting a network camera with refresh degradation |
| WO2006033514A2 (en) * | 2004-09-22 | 2006-03-30 | Electronics And Telecommunications Research Institute | Internal data structure of mobile terminal for qos-based uplink data transmission, and operational methods thereof |
| US7024488B1 (en) * | 2001-04-12 | 2006-04-04 | Ipix Corporation | Method and apparatus for hosting a network camera |
| US20060083226A1 (en) * | 2004-10-18 | 2006-04-20 | At&T Corp. | Queueing technique for multiple sources and multiple priorities |
| WO2006062887A1 (en) * | 2004-12-09 | 2006-06-15 | The Boeing Company | Network centric quality of service using active network technology |
| US7072300B1 (en) * | 2001-03-23 | 2006-07-04 | Advanced Micro Devices, Inc. | Action tag generation within a network based on priority or differential services information |
| US20060149854A1 (en) * | 2002-01-31 | 2006-07-06 | Steven Rudkin | Network service selection |
| US7076085B1 (en) | 2001-04-12 | 2006-07-11 | Ipix Corp. | Method and apparatus for hosting a network camera including a heartbeat mechanism |
| US20060248372A1 (en) * | 2005-04-29 | 2006-11-02 | International Business Machines Corporation | Intelligent resource provisioning based on on-demand weight calculation |
| US20060256721A1 (en) * | 2005-05-13 | 2006-11-16 | Yahoo! Inc. | Dynamically selecting codecs for managing an audio message |
| US7177448B1 (en) | 2001-04-12 | 2007-02-13 | Ipix Corporation | System and method for selecting and transmitting images of interest to a user |
| US20070036163A1 (en) * | 2001-05-31 | 2007-02-15 | Dibiasio Michael V | Resource sharing among multiple RSVP sessions |
| US20070058650A1 (en) * | 2005-08-09 | 2007-03-15 | International Business Machines Corporation | Resource buffer sizing under replenishment for services |
| US7206282B1 (en) * | 2001-05-29 | 2007-04-17 | F5 Networks, Inc. | Method and apparatus to balance flow loads in a multipurpose networking device |
| US20070094412A1 (en) * | 2001-06-14 | 2007-04-26 | Nortel Networks Limited | Providing telephony services to terminals behind a firewall and/or a network address translator |
| US7225271B1 (en) * | 2001-06-29 | 2007-05-29 | Cisco Technology, Inc. | System and method for recognizing application-specific flows and assigning them to queues |
| US20070121500A1 (en) * | 2005-11-29 | 2007-05-31 | Alcatel | Communication session admission control systems and methods |
| US7237020B1 (en) | 2002-01-25 | 2007-06-26 | Hewlett-Packard Development Company, L.P. | Integer programming technique for verifying and reprovisioning an interconnect fabric design |
| CN100337456C (en) * | 2004-11-23 | 2007-09-12 | 毛德操 | Method for raising safety of IP network through router signature |
| US7277944B1 (en) * | 2001-05-31 | 2007-10-02 | Cisco Technology, Inc. | Two phase reservations for packet networks |
| WO2007113109A1 (en) * | 2006-03-30 | 2007-10-11 | Nokia Siemens Networks Gmbh & Co. Kg | Network access control using an additional traffic class in a communication network |
| US7307954B1 (en) * | 2000-06-23 | 2007-12-11 | Nokia Corporation | Differentiated service network and method of operating a differentiated service network |
| US7310761B2 (en) * | 2003-04-26 | 2007-12-18 | Samsung Electronics Co., Ltd. | Apparatus and method for retransmitting data packets in mobile ad hoc network environment |
| US20070297335A1 (en) * | 1997-12-12 | 2007-12-27 | Level 3 Communications, Llc | Secure network architecture with quality of service |
| US7324442B1 (en) * | 2000-02-28 | 2008-01-29 | The Board Of Trustees Of The Leland Stanford Junior University | Active queue management toward fair bandwidth allocation |
| US20080123534A1 (en) * | 2002-10-18 | 2008-05-29 | Cariden Technologies, Inc. | Metric optimization for traffic engineering in a metric-routed network |
| US20080225889A1 (en) * | 2007-03-14 | 2008-09-18 | Cisco Technology, Inc. | Admission control for virtualized services in routers |
| US20080273461A1 (en) * | 2005-03-29 | 2008-11-06 | International Business Machines Corporation | Network system, traffic balancing method, network monitoring device and host |
| US7450507B2 (en) * | 2002-06-05 | 2008-11-11 | Lucent Technologies Inc. | Hierarchal rate-limiting at a network node that utilizes an infinity rate-limit check |
| US7464163B1 (en) * | 2000-07-27 | 2008-12-09 | International Business Machines Corporation | Service provisioning via attribute-based subscription |
| US7475141B1 (en) * | 2001-07-31 | 2009-01-06 | Arbor Networks, Inc. | Distributed service level management for network traffic |
| US20090181673A1 (en) * | 2004-12-06 | 2009-07-16 | Motorola, Inc. | Method, apparatus and base station for determining a radio link characteristic |
| US7774468B1 (en) | 2000-07-28 | 2010-08-10 | Siddhartha Nag | Network traffic admission control |
| US7787370B1 (en) * | 2001-09-06 | 2010-08-31 | Nortel Networks Limited | Technique for adaptively load balancing connections in multi-link trunks |
| US20100316022A1 (en) * | 2009-06-16 | 2010-12-16 | Verizon Patent And Licensing Inc. | Communication routing |
| US7886054B1 (en) * | 2000-10-11 | 2011-02-08 | Siddhartha Nag | Graphical user interface (GUI) for administering a network implementing media aggregation |
| US7940746B2 (en) | 2004-08-24 | 2011-05-10 | Comcast Cable Holdings, Llc | Method and system for locating a voice over internet protocol (VoIP) device connected to a network |
| US7953888B2 (en) | 1999-06-18 | 2011-05-31 | Level 3 Communications, Llc | On-demand overlay routing for computer-based communication networks |
| US8026944B1 (en) | 2001-04-12 | 2011-09-27 | Sony Corporation | Method and apparatus for hosting a network camera with image degradation |
| US20120075994A1 (en) * | 2001-04-02 | 2012-03-29 | International Business Machines Corporation | Method and apparatus for managing aggregate bandwidth at a server |
| US20120102133A1 (en) * | 2009-06-19 | 2012-04-26 | Zte Corporation | Device And Method For Enabling Hierarchical Quality Of Service Services |
| US8428074B2 (en) | 2005-04-29 | 2013-04-23 | Prom Ks Mgmt Limited Liability Company | Back-to back H.323 proxy gatekeeper |
| US8458332B2 (en) | 2000-07-28 | 2013-06-04 | Prom Ks Mgmt Limited Liability Company | Multiplexing several individual application sessions over a pre-allocated reservation protocol session |
| US8595478B2 (en) | 2000-07-10 | 2013-11-26 | AlterWAN Inc. | Wide area network with high quality of service |
| US20140092744A1 (en) * | 2010-11-19 | 2014-04-03 | Cisco Technology, Inc. | Dynamic Queuing and Pinning to Improve Quality of Service on Uplinks in a Virtualized Environment |
| EP2779544A1 (en) * | 2013-03-15 | 2014-09-17 | Comcast Cable Communications, LLC | Remote latency adjustment |
| US20140344473A1 (en) * | 2013-05-16 | 2014-11-20 | Power-All Networks Limited | Transmission management device, system, and method |
| US20140341033A1 (en) * | 2013-05-16 | 2014-11-20 | Power-All Networks Limited | Transmission management device, system, and method |
| US20150074234A1 (en) * | 2013-09-11 | 2015-03-12 | Electronics And Telecommunications Research Institute | Content system and method for chunk-based content delivery |
| US20150200838A1 (en) * | 2014-01-10 | 2015-07-16 | Juniper Networks, Inc. | Dynamic end-to-end network path setup across multiple network layers with network service chaining |
| US20150381496A1 (en) * | 2014-06-26 | 2015-12-31 | Fujitsu Limited | Communication apparatus and communication method |
| US9286294B2 (en) | 1992-12-09 | 2016-03-15 | Comcast Ip Holdings I, Llc | Video and digital multimedia aggregator content suggestion engine |
| CN105939290A (en) * | 2012-08-14 | 2016-09-14 | 华为技术有限公司 | Resource allocation method and device |
| US20170155574A1 (en) * | 2015-12-01 | 2017-06-01 | Transition Networks, Inc. | Connection qualified link pass through |
| US9813641B2 (en) | 2000-06-19 | 2017-11-07 | Comcast Ip Holdings I, Llc | Method and apparatus for targeting of interactive virtual objects |
| US10140433B2 (en) | 2001-08-03 | 2018-11-27 | Comcast Ip Holdings I, Llc | Video and digital multimedia aggregator |
| US10349096B2 (en) | 2001-08-03 | 2019-07-09 | Comcast Ip Holdings I, Llc | Video and digital multimedia aggregator content coding and formatting |
| US10666565B2 (en) * | 2018-06-08 | 2020-05-26 | Citrix Systems, Inc. | Method to measure relative QOS gains and to reduce the variance in QOS for similar connections for during bandwidth contention |
| US11510073B2 (en) * | 2020-10-23 | 2022-11-22 | At&T Intellectual Property I, L.P. | Mobility backhaul bandwidth on demand |
| CN116094992A (en) * | 2022-12-23 | 2023-05-09 | 中电信数智科技有限公司 | Message forwarding method, storage medium and device based on worksheet scene |
| US11956852B2 (en) | 2022-02-11 | 2024-04-09 | Comcast Cable Communications, Llc | Physical location management for voice over packet communication |
Families Citing this family (33)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP3479908B2 (en) * | 2000-03-24 | 2003-12-15 | 日本電気株式会社 | Communication quality assurance path setting method for VoIP and network management system |
| GB0031536D0 (en) * | 2000-12-22 | 2001-02-07 | Nokia Networks Oy | Selecting data packets |
| US8762568B1 (en) * | 2001-07-06 | 2014-06-24 | Cisco Technology, Inc. | Method and apparatus for inter-zone restoration |
| US7457862B2 (en) * | 2001-10-22 | 2008-11-25 | Avaya, Inc. | Real time control protocol session matching |
| US7428216B2 (en) * | 2002-01-15 | 2008-09-23 | Avaya Inc. | Method and apparatus for policy and admission control in packet-based communication systems |
| US7489687B2 (en) * | 2002-04-11 | 2009-02-10 | Avaya. Inc. | Emergency bandwidth allocation with an RSVP-like protocol |
| WO2004025394A2 (en) * | 2002-09-13 | 2004-03-25 | Passave Ltd. | Operations method in an ethernet passive optical network that includes a network unit with multiple entities |
| US8176154B2 (en) * | 2002-09-30 | 2012-05-08 | Avaya Inc. | Instantaneous user initiation voice quality feedback |
| US20040073690A1 (en) | 2002-09-30 | 2004-04-15 | Neil Hepworth | Voice over IP endpoint call admission |
| US7359979B2 (en) | 2002-09-30 | 2008-04-15 | Avaya Technology Corp. | Packet prioritization and associated bandwidth and buffer management techniques for audio over IP |
| US7411905B1 (en) * | 2003-09-05 | 2008-08-12 | Sprint Communications Company L.P. | Segmented IP backbone network access |
| US7978827B1 (en) | 2004-06-30 | 2011-07-12 | Avaya Inc. | Automatic configuration of call handling based on end-user needs and characteristics |
| US7463584B2 (en) * | 2004-08-03 | 2008-12-09 | Nortel Networks Limited | System and method for hub and spoke virtual private network |
| US7730519B2 (en) * | 2004-09-17 | 2010-06-01 | At&T Intellectual Property I, L.P. | Detection of encrypted packet streams using feedback probing |
| US7761705B2 (en) * | 2004-09-17 | 2010-07-20 | At&T Intellectual Property I, L.P. | Detection of encrypted packet streams |
| US7451309B2 (en) | 2004-09-17 | 2008-11-11 | At&T Intellectual Property L.P. | Signature specification for encrypted packet streams |
| US8332938B2 (en) | 2004-09-17 | 2012-12-11 | At&T Intellectual Property I, L.P. | Detection of encrypted packet streams using a timer |
| US20060117020A1 (en) * | 2004-12-01 | 2006-06-01 | John Toebes | Arrangement for selecting a server to provide distributed services from among multiple servers based on a location of a client device |
| US7664099B1 (en) | 2004-12-30 | 2010-02-16 | At&T Corp. | Method and apparatus for providing shared services |
| US7623548B2 (en) * | 2005-12-22 | 2009-11-24 | At&T Intellectual Property, I,L.P. | Methods, systems, and computer program products for managing access resources in an internet protocol network |
| WO2007140482A2 (en) * | 2006-05-31 | 2007-12-06 | Riverbed Technology, Inc. | Service curve mapping |
| US8285650B2 (en) * | 2006-06-13 | 2012-10-09 | At&T Intellectual Property I, Lp | Method and apparatus for billing data services |
| US8462629B2 (en) * | 2006-06-14 | 2013-06-11 | Riverbed Technology, Inc. | Cooperative operation of network transport and network quality of service modules |
| DE602006004869D1 (en) * | 2006-09-01 | 2009-03-05 | Alcatel Lucent | Procedure for creating an IPTV service |
| US7796521B2 (en) * | 2006-11-09 | 2010-09-14 | Alcatel-Lucent Usa Inc. | Method and apparatus for policing bandwidth usage for a home network |
| US7617337B1 (en) | 2007-02-06 | 2009-11-10 | Avaya Inc. | VoIP quality tradeoff system |
| US8706878B1 (en) | 2008-08-21 | 2014-04-22 | United Services Automobile Association | Preferential loading in data centers |
| US8218751B2 (en) | 2008-09-29 | 2012-07-10 | Avaya Inc. | Method and apparatus for identifying and eliminating the source of background noise in multi-party teleconferences |
| US9036474B2 (en) * | 2010-06-08 | 2015-05-19 | Alcatel Lucent | Communication available transport network bandwidth to L2 ethernet nodes |
| US9001651B2 (en) * | 2012-02-06 | 2015-04-07 | Verizon Patent And Licensing Inc. | Method for call admission control in MPLS networks |
| US9769082B2 (en) | 2015-04-01 | 2017-09-19 | Honeywell International Inc. | System and method for network bandwidth, buffers and timing management using hybrid scheduling of traffic with different priorities and guarantees |
| US9769075B2 (en) | 2015-04-01 | 2017-09-19 | Honeywell International Inc. | Interference cognizant network scheduling |
| US9762501B2 (en) | 2015-04-01 | 2017-09-12 | Honeywell International Inc. | Systematic hybrid network scheduling for multiple traffic classes with host timing and phase constraints |
Citations (13)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US6011780A (en) * | 1997-05-23 | 2000-01-04 | Stevens Institute Of Technology | Transparant non-disruptable ATM network |
| US6046981A (en) * | 1997-02-28 | 2000-04-04 | Nec Usa, Inc. | Multi-class connection admission control method for Asynchronous Transfer Mode (ATM) switches |
| US6141319A (en) * | 1996-04-10 | 2000-10-31 | Nec Usa, Inc. | Link based alternative routing scheme for network restoration under failure |
| US6222820B1 (en) * | 1998-05-28 | 2001-04-24 | 3Com Corporation | Method of VCC/VPC redundancy for asynchronous transfer mode networks |
| US6240463B1 (en) * | 1998-11-24 | 2001-05-29 | Lucent Technologies Inc. | Router placement methods and apparatus for designing IP networks with performance guarantees |
| US6363319B1 (en) * | 1999-08-31 | 2002-03-26 | Nortel Networks Limited | Constraint-based route selection using biased cost |
| US6408005B1 (en) * | 1997-09-05 | 2002-06-18 | Nec Usa, Inc. | Dynamic rate control scheduler for ATM networks |
| US6442138B1 (en) * | 1996-10-03 | 2002-08-27 | Nortel Networks Limited | Method and apparatus for controlling admission of connection requests |
| US6449253B1 (en) * | 1997-10-29 | 2002-09-10 | Telcordia Technologies, Inc. | Method and system for dynamic allocation of bandwidth in asynchronous transfer mode (ATM) switching systems |
| US6493318B1 (en) * | 1998-05-04 | 2002-12-10 | Hewlett-Packard Company | Cost propagation switch protocols |
| US6493317B1 (en) * | 1998-12-18 | 2002-12-10 | Cisco Technology, Inc. | Traffic engineering technique for routing inter-class traffic in a computer network |
| US6504819B2 (en) * | 1997-10-03 | 2003-01-07 | Alcatel Canada Inc. | Classes of service in an MPOA network |
| US6529499B1 (en) * | 1998-09-22 | 2003-03-04 | Lucent Technologies Inc. | Method for providing quality of service for delay sensitive traffic over IP networks |
Family Cites Families (13)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| JP2982828B2 (en) * | 1994-09-17 | 1999-11-29 | インターナシヨナル・ビジネス・マシーンズ・コーポレーシヨン | Flow control method and apparatus for cell based communication network |
| US6591299B2 (en) * | 1997-11-25 | 2003-07-08 | Packeteer, Inc. | Method for automatically classifying traffic with enhanced hierarchy in a packet communications network |
| AU1421799A (en) * | 1997-11-25 | 1999-06-15 | Packeteer, Inc. | Method for automatically classifying traffic in a packet communications network |
| US6259699B1 (en) * | 1997-12-30 | 2001-07-10 | Nexabit Networks, Llc | System architecture for and method of processing packets and/or cells in a common switch |
| US6483839B1 (en) * | 1998-03-18 | 2002-11-19 | Conexant Systems, Inc. | Apparatus and method for scheduling multiple and simultaneous traffic in guaranteed frame rate in ATM communication system |
| US6594268B1 (en) * | 1999-03-11 | 2003-07-15 | Lucent Technologies Inc. | Adaptive routing system and method for QOS packet networks |
| US6717912B1 (en) * | 1999-05-28 | 2004-04-06 | Network Equipment Technologies, Inc. | Fair discard system |
| US6721270B1 (en) * | 1999-08-09 | 2004-04-13 | Lucent Technologies Inc. | Multicommodity flow method for designing traffic distribution on a multiple-service packetized network |
| US6553568B1 (en) * | 1999-09-29 | 2003-04-22 | 3Com Corporation | Methods and systems for service level agreement enforcement on a data-over cable system |
| US6760334B1 (en) * | 2000-06-13 | 2004-07-06 | Cisco Technology, Inc. | Method and apparatus for oversubscription of permanent virtual circuits |
| US6658479B1 (en) * | 2000-06-30 | 2003-12-02 | Sun Microsystems, Inc. | Load-balanced anycasting and routing in a network |
| US6697335B1 (en) * | 2000-07-27 | 2004-02-24 | Lucent Technologies Inc. | Quality of service routing in information networks over paths having performance-dependent costs |
| US6636482B2 (en) * | 2001-03-08 | 2003-10-21 | Arris International, Inc. | Method and apparatus for controlling traffic loading of different service levels in a cable data system |
-
1999
- 1999-12-30 US US09/475,512 patent/US6744767B1/en not_active Expired - Fee Related
-
2004
- 2004-03-23 US US10/806,742 patent/US6973033B1/en not_active Expired - Fee Related
Patent Citations (13)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US6141319A (en) * | 1996-04-10 | 2000-10-31 | Nec Usa, Inc. | Link based alternative routing scheme for network restoration under failure |
| US6442138B1 (en) * | 1996-10-03 | 2002-08-27 | Nortel Networks Limited | Method and apparatus for controlling admission of connection requests |
| US6046981A (en) * | 1997-02-28 | 2000-04-04 | Nec Usa, Inc. | Multi-class connection admission control method for Asynchronous Transfer Mode (ATM) switches |
| US6011780A (en) * | 1997-05-23 | 2000-01-04 | Stevens Institute Of Technology | Transparant non-disruptable ATM network |
| US6408005B1 (en) * | 1997-09-05 | 2002-06-18 | Nec Usa, Inc. | Dynamic rate control scheduler for ATM networks |
| US6504819B2 (en) * | 1997-10-03 | 2003-01-07 | Alcatel Canada Inc. | Classes of service in an MPOA network |
| US6449253B1 (en) * | 1997-10-29 | 2002-09-10 | Telcordia Technologies, Inc. | Method and system for dynamic allocation of bandwidth in asynchronous transfer mode (ATM) switching systems |
| US6493318B1 (en) * | 1998-05-04 | 2002-12-10 | Hewlett-Packard Company | Cost propagation switch protocols |
| US6222820B1 (en) * | 1998-05-28 | 2001-04-24 | 3Com Corporation | Method of VCC/VPC redundancy for asynchronous transfer mode networks |
| US6529499B1 (en) * | 1998-09-22 | 2003-03-04 | Lucent Technologies Inc. | Method for providing quality of service for delay sensitive traffic over IP networks |
| US6240463B1 (en) * | 1998-11-24 | 2001-05-29 | Lucent Technologies Inc. | Router placement methods and apparatus for designing IP networks with performance guarantees |
| US6493317B1 (en) * | 1998-12-18 | 2002-12-10 | Cisco Technology, Inc. | Traffic engineering technique for routing inter-class traffic in a computer network |
| US6363319B1 (en) * | 1999-08-31 | 2002-03-26 | Nortel Networks Limited | Constraint-based route selection using biased cost |
Non-Patent Citations (12)
| Title |
|---|
| A method for Setting an Alternative Label Switched Paths to Handle Fast Reroute, Haskin et al, IETF, Dec. 1999.* * |
| A. K. Parekh and R. C. Gallager, "A Generalized Processor Sharing Approach to Flow Control in Integrated Services Network: The Multiple Node Case." IEEE/ACM Transactions on Networking. Apr. 1994, pp. 137-150. |
| A. K. Parekh and R. C. Gallager, "A Generalized Processor Sharing Approach to Flow Control in Integrated Services Networks: The Single-Node Case," IEEE/ACM Transactions on Networking, Jun. 1993, pp. 344-357. |
| IETF Multiprotocol Label Switching (MPLS) Architecture, Faucheur, 1998 IEEE.* * |
| J. Padhye, V. Firoiu, D. Towsley and J. Kurose, "Modeling TCP Throughput: A Simple Model and its Empirical Validation," In Proceedings of Sigcomm 98, pp. 1-12. |
| J. Wroclawski, "Specification of the Controlled-Load Network Element Service," IETF RFC2211, Sep. 1997, pp. 1-19. |
| Routing Subject to Quality of Service Constraints in Integrated Communication Networks, IEEE Network, Jul./Aug. 1995.* * |
| S. Blake, D. Black, M. Carlson, E. Davies, Z. Wang and W. Weiss, "An Architecture for Differentiated Services," RFC2475, Dec. 1998, pp. 1-36. |
| S. Floyd and V. Jacobson, "Random Early Detection Gateways for Congestion Avoidance," IEEE/ACM Transaction on Networking, Aug. 1993, pp. 1-32. |
| S. Shenker, C. Partridge and R. Guerin, "Specification of Guaranteed Quality of Service," IETF RFC2212, Sep. 1997, pp. 1-20. |
| Tag Switching Architecture Overview, Rekhter et al. , Proceeding of the IEEE, vol. 85, No. 12, Dec. 1997.* * |
| V. Jacobson, K. Nichols, K. Poduri, "An Expedited Forwarding PHB", IETF RFC2598, Jun. 1999, pp. 1-10. |
Cited By (200)
| Publication number | Priority date | Publication date | Assignee | Title |
|---|---|---|---|---|
| US9286294B2 (en) | 1992-12-09 | 2016-03-15 | Comcast Ip Holdings I, Llc | Video and digital multimedia aggregator content suggestion engine |
| US20070297335A1 (en) * | 1997-12-12 | 2007-12-27 | Level 3 Communications, Llc | Secure network architecture with quality of service |
| US8599697B2 (en) | 1999-06-18 | 2013-12-03 | Level 3 Communications, Llc | Overlay network |
| US7953888B2 (en) | 1999-06-18 | 2011-05-31 | Level 3 Communications, Llc | On-demand overlay routing for computer-based communication networks |
| US20020126579A1 (en) * | 1999-09-20 | 2002-09-12 | Gualtieri Devlin M. | Steered beam ultraonic sensor for object location and classification |
| US6961307B1 (en) * | 1999-12-06 | 2005-11-01 | Nortel Networks Limited | Queue management mechanism for proportional loss rate differentiation |
| US6959335B1 (en) * | 1999-12-22 | 2005-10-25 | Nortel Networks Limited | Method of provisioning a route in a connectionless communications network such that a guaranteed quality of service is provided |
| US6934259B2 (en) * | 2000-01-18 | 2005-08-23 | At&T Corp | Apparatus and method for designing a network |
| US7626945B1 (en) * | 2000-01-18 | 2009-12-01 | At&T Intellectual Property Ii, L.P. | System and method for designing a network |
| US20100074115A1 (en) * | 2000-01-18 | 2010-03-25 | At&T Corp. | System and Method for Designing a Network |
| US7965654B2 (en) | 2000-01-18 | 2011-06-21 | At&T Intellectual Property Ii, L.P. | System and method for designing a network |
| US20040095887A1 (en) * | 2000-01-18 | 2004-05-20 | At&T Corp. | Apparatus and method for designing a network |
| US20010051992A1 (en) * | 2000-02-24 | 2001-12-13 | Brian Yang | Unified algorithm for frame scheduling and buffer management in differentiated services networks |
| US6990529B2 (en) * | 2000-02-24 | 2006-01-24 | Zarlink Semiconductor V.N., Inc. | Unified algorithm for frame scheduling and buffer management in differentiated services networks |
| US7324442B1 (en) * | 2000-02-28 | 2008-01-29 | The Board Of Trustees Of The Leland Stanford Junior University | Active queue management toward fair bandwidth allocation |
| US20010019554A1 (en) * | 2000-03-06 | 2001-09-06 | Yuji Nomura | Label switch network system |
| US7035259B2 (en) * | 2000-03-06 | 2006-04-25 | Fujitsu Limited | Label switch network system |
| US20010023443A1 (en) * | 2000-03-20 | 2001-09-20 | International Business Machines Corporation | System and method for reserving a virtual connection in an IP network |
| US7320034B2 (en) * | 2000-03-20 | 2008-01-15 | International Business Machines Corporation | System and method for reserving a virtual connection in an IP network |
| US20080040469A1 (en) * | 2000-03-30 | 2008-02-14 | Nec Corporation | Quality assured network service provision system compatible with a multi-domain network and service provision method and service broker device |
| US7254645B2 (en) * | 2000-03-30 | 2007-08-07 | Nec Corporation | Quality assured network service provision system compatible with a multi-domain network and service provision method and service broker device |
| US8214533B2 (en) | 2000-03-30 | 2012-07-03 | Nec Corporation | Quality assured network service provision system compatible with a multi-domain network and service provision method and service broker device |
| US20010027484A1 (en) * | 2000-03-30 | 2001-10-04 | Nec Corporation | Quality assured network service provision system compatible with a multi-domain network and service provision method and service broker device |
| US9813641B2 (en) | 2000-06-19 | 2017-11-07 | Comcast Ip Holdings I, Llc | Method and apparatus for targeting of interactive virtual objects |
| US7307954B1 (en) * | 2000-06-23 | 2007-12-11 | Nokia Corporation | Differentiated service network and method of operating a differentiated service network |
| US20020059427A1 (en) * | 2000-07-07 | 2002-05-16 | Hitachi, Ltd. | Apparatus and method for dynamically allocating computer resources based on service contract with user |
| US9015471B2 (en) | 2000-07-10 | 2015-04-21 | Alterwan, Inc. | Inter-autonomous networking involving multiple service providers |
| US9985800B2 (en) | 2000-07-10 | 2018-05-29 | Alterwan, Inc. | VPN usage to create wide area network backbone over the internet |
| US8595478B2 (en) | 2000-07-10 | 2013-11-26 | AlterWAN Inc. | Wide area network with high quality of service |
| US9525620B2 (en) | 2000-07-10 | 2016-12-20 | Alterwan, Inc. | Private tunnel usage to create wide area network backbone over the internet |
| US9667534B2 (en) | 2000-07-10 | 2017-05-30 | Alterwan, Inc. | VPN usage to create wide area network backbone over the internet |
| US20040078733A1 (en) * | 2000-07-13 | 2004-04-22 | Lewis Lundy M. | Method and apparatus for monitoring and maintaining user-perceived quality of service in a communications network |
| US7689857B2 (en) * | 2000-07-13 | 2010-03-30 | Computer Associates Think, Inc. | Method and apparatus for monitoring and maintaining user-perceived quality of service in a communications network |
| US7464163B1 (en) * | 2000-07-27 | 2008-12-09 | International Business Machines Corporation | Service provisioning via attribute-based subscription |
| US8929394B2 (en) | 2000-07-28 | 2015-01-06 | Prom Ks Mgmt Limited Liability Company | End-to-end service quality for latency-intensive internet protocol (IP) applications in a heterogeneous, multi-vendor environment |
| US20090296734A1 (en) * | 2000-07-28 | 2009-12-03 | Siddhartha Nag | End-To-End Service Quality for Latency-Intensive Internet Protocol (IP) Applications in a Heterogeneous, Multi-Vendor Environment |
| US8032646B2 (en) | 2000-07-28 | 2011-10-04 | Prom KS Limited Liability Company | Administering a communication network |
| US7788354B2 (en) | 2000-07-28 | 2010-08-31 | Siddhartha Nag | End-to-end service quality in a voice over Internet Protocol (VoIP) Network |
| US8315275B2 (en) | 2000-07-28 | 2012-11-20 | Prom Ks Mgmt Limited Liability Company | End-to-end service quality for latency-intensive internet protocol (IP) applications in a heterogeneous, multi-vendor environment |
| US20040172464A1 (en) * | 2000-07-28 | 2004-09-02 | Siddhartha Nag | End-to-end service quality for latency-intensive internet protocol (IP) applications in a heterogeneous, multi-vendor environment |
| US7774468B1 (en) | 2000-07-28 | 2010-08-10 | Siddhartha Nag | Network traffic admission control |
| US8458332B2 (en) | 2000-07-28 | 2013-06-04 | Prom Ks Mgmt Limited Liability Company | Multiplexing several individual application sessions over a pre-allocated reservation protocol session |
| US20040196855A1 (en) * | 2000-10-03 | 2004-10-07 | U4Ea Technologies Limited | Prioritizing data with flow control |
| US7535835B2 (en) * | 2000-10-03 | 2009-05-19 | U4Ea Technologies Limited | Prioritizing data with flow control |
| US8185640B2 (en) | 2000-10-11 | 2012-05-22 | Prominence Networks, Inc. | Graphical user interface (GUI) for administering a voice over internet protocol (VOIP) network implementing media aggregation |
| US20120224586A1 (en) * | 2000-10-11 | 2012-09-06 | Prom Ks Mgmt Limited Liability Company | Graphical user interface (gui) for administering a network implementing media aggregation |
| US8918523B2 (en) * | 2000-10-11 | 2014-12-23 | Prom Ks Mgmt Limited Liability Company | Graphical user interface (GUI) for administering a network implementing media aggregation |
| US7886054B1 (en) * | 2000-10-11 | 2011-02-08 | Siddhartha Nag | Graphical user interface (GUI) for administering a network implementing media aggregation |
| US6862291B2 (en) * | 2000-11-03 | 2005-03-01 | Telcordia Technologies, Inc. | Method and system for quality of service provisioning for IP virtual private networks |
| US20020145982A1 (en) * | 2000-11-03 | 2002-10-10 | Talpade Rajesh Rasik | Method and system for quality of service provisioning for IP virtual private networks |
| US7032013B2 (en) | 2000-11-06 | 2006-04-18 | Hewlett-Packard Development Company, L.P. | Reliability for interconnect fabrics |
| US7233983B2 (en) | 2000-11-06 | 2007-06-19 | Hewlett-Packard Development Company, L.P. | Reliability for interconnect fabrics |
| US7076537B2 (en) | 2000-11-06 | 2006-07-11 | Hewlett-Packard Development Company, L.P. | Designing interconnect fabrics |
| US20020091804A1 (en) * | 2000-11-06 | 2002-07-11 | Ward Julie Ann | Reliability for interconnect fabrics |
| US7000011B1 (en) * | 2000-11-06 | 2006-02-14 | Hewlett-Packard Development Company, Lp. | Designing interconnect fabrics |
| US20020091845A1 (en) * | 2000-11-06 | 2002-07-11 | Ward Julie Ann | Reliability for interconnect fabrics |
| US20020075863A1 (en) * | 2000-12-20 | 2002-06-20 | Yoshimi Nakagawa | Pathsize control method and operation of transmission apparatus |
| US7054334B2 (en) * | 2000-12-20 | 2006-05-30 | Hitachi, Ltd. | Pathsize control method and operation of transmission apparatus |
| US20020118646A1 (en) * | 2000-12-21 | 2002-08-29 | Jean-Francois Saint Etienne | Device and process for flow control in a switched network |
| US20020093925A1 (en) * | 2001-01-18 | 2002-07-18 | Chuah Mooi Choo | Universal mobile telecommunications system (UMTS) quality of service (QoS) supporting variable QoS negotiation |
| US7668176B2 (en) * | 2001-01-18 | 2010-02-23 | Alcatel-Lucent Usa Inc. | Universal mobile telecommunications system (UMTS) quality of service (QoS) supporting variable QoS negotiation |
| US6996062B1 (en) * | 2001-02-28 | 2006-02-07 | 3Com Corporation | Policy-based weighted random early detection method for avoiding congestion in internet traffic |
| US20020124091A1 (en) * | 2001-03-01 | 2002-09-05 | Yoshitoshi Kurose | Network service setting system, network service providing method and communication service |
| US7719963B2 (en) * | 2001-03-06 | 2010-05-18 | Pluris, Inc. | System for fabric packet control |
| US20040223456A1 (en) * | 2001-03-06 | 2004-11-11 | Deepak Mansharamani | System for fabric packet Control |
| US20040090914A1 (en) * | 2001-03-07 | 2004-05-13 | Briscoe Robert J | Communications network |
| US7072300B1 (en) * | 2001-03-23 | 2006-07-04 | Advanced Micro Devices, Inc. | Action tag generation within a network based on priority or differential services information |
| US20120075994A1 (en) * | 2001-04-02 | 2012-03-29 | International Business Machines Corporation | Method and apparatus for managing aggregate bandwidth at a server |
| US7177448B1 (en) | 2001-04-12 | 2007-02-13 | Ipix Corporation | System and method for selecting and transmitting images of interest to a user |
| US7076085B1 (en) | 2001-04-12 | 2006-07-11 | Ipix Corp. | Method and apparatus for hosting a network camera including a heartbeat mechanism |
| US8026944B1 (en) | 2001-04-12 | 2011-09-27 | Sony Corporation | Method and apparatus for hosting a network camera with image degradation |
| US7024488B1 (en) * | 2001-04-12 | 2006-04-04 | Ipix Corporation | Method and apparatus for hosting a network camera |
| US7015949B1 (en) | 2001-04-12 | 2006-03-21 | Ipix Corporation | Method and apparatus for hosting a network camera with refresh degradation |
| US7707271B2 (en) | 2001-04-19 | 2010-04-27 | British Telecommunications Plc | Delivering personalized content data via local network |
| US20040117426A1 (en) * | 2001-04-19 | 2004-06-17 | Steven Rudkin | Communications network |
| US20050044263A1 (en) * | 2001-05-08 | 2005-02-24 | Wei Zhang | Scheduling method of realizing the quality of service of router in integrated service |
| US7355972B2 (en) * | 2001-05-08 | 2008-04-08 | Huawei Technologies Co., Ltd. | Scheduling method of realizing the quality of service of router in integrated service |
| US20020188648A1 (en) * | 2001-05-08 | 2002-12-12 | James Aweya | Active queue management with flow proportional buffering |
| US6901593B2 (en) * | 2001-05-08 | 2005-05-31 | Nortel Networks Limited | Active queue management with flow proportional buffering |
| US7206282B1 (en) * | 2001-05-29 | 2007-04-17 | F5 Networks, Inc. | Method and apparatus to balance flow loads in a multipurpose networking device |
| US7580353B1 (en) | 2001-05-29 | 2009-08-25 | F5 Networks, Inc. | Method and apparatus to balance flow loads in a multipurpose networking device |
| US7054327B2 (en) * | 2001-05-30 | 2006-05-30 | Lucent Technologies Inc. | Method of providing quality of service (QOS) to voice applications in routed IP networks |
| US20020181401A1 (en) * | 2001-05-30 | 2002-12-05 | Hassan Hagirahim | Method of providing quality of service (QOS) to voice applications in routed IP networks |
| US7454504B2 (en) | 2001-05-31 | 2008-11-18 | Cisco Technology, Inc. | Resource sharing among multiple RSVP sessions |
| US7277944B1 (en) * | 2001-05-31 | 2007-10-02 | Cisco Technology, Inc. | Two phase reservations for packet networks |
| US7281043B1 (en) * | 2001-05-31 | 2007-10-09 | Cisco Technology, Inc. | System for sharing resources among RSVP sessions |
| US20070036163A1 (en) * | 2001-05-31 | 2007-02-15 | Dibiasio Michael V | Resource sharing among multiple RSVP sessions |
| US6977905B1 (en) | 2001-06-01 | 2005-12-20 | Cisco Technology, Inc. | Network with self regulating quality of service (QoS) |
| US7233578B1 (en) | 2001-06-01 | 2007-06-19 | Cisco Technology, Inc. | Network with self regulating quality of service (QoS) |
| US8397276B2 (en) | 2001-06-14 | 2013-03-12 | Genband Us Llc | Protecting a network from unauthorized access |
| US8108553B2 (en) | 2001-06-14 | 2012-01-31 | Rockstar Bidco, LP | Providing network address translation information |
| US20070094412A1 (en) * | 2001-06-14 | 2007-04-26 | Nortel Networks Limited | Providing telephony services to terminals behind a firewall and/or a network address translator |
| US7684317B2 (en) * | 2001-06-14 | 2010-03-23 | Nortel Networks Limited | Protecting a network from unauthorized access |
| US20070053289A1 (en) * | 2001-06-14 | 2007-03-08 | Nortel Networks Limited | Protecting a network from unauthorized access |
| US20100175110A1 (en) * | 2001-06-14 | 2010-07-08 | March Sean W | Protecting a network from unauthorized access |
| US20070192508A1 (en) * | 2001-06-14 | 2007-08-16 | Nortel Networks Limited | Providing network address translation information |
| US7940654B2 (en) | 2001-06-14 | 2011-05-10 | Genband Us Llc | Protecting a network from unauthorized access |
| US8244876B2 (en) | 2001-06-14 | 2012-08-14 | Rockstar Bidco, LP | Providing telephony services to terminals behind a firewall and/or a network address translator |
| US8484359B2 (en) | 2001-06-14 | 2013-07-09 | Rockstar Consortium Us Lp | Providing telephony services to terminals behind a firewall and/or a network address translator |
| US20030043740A1 (en) * | 2001-06-14 | 2003-03-06 | March Sean W. | Protecting a network from unauthorized access |
| US20070192507A1 (en) * | 2001-06-29 | 2007-08-16 | Dibiasio Michael V | System and method for recognizing and assigning application-specific flows |
| US7225271B1 (en) * | 2001-06-29 | 2007-05-29 | Cisco Technology, Inc. | System and method for recognizing application-specific flows and assigning them to queues |
| US7934016B2 (en) | 2001-06-29 | 2011-04-26 | Cisco Technology, Inc. | System and method for recognizing and assigning application-specific flows |
| US20050286559A1 (en) * | 2001-07-02 | 2005-12-29 | Cisco Technology, Inc., A California Corporation | Method and system for sharing over-allocated bandwidth between different classes of service in a wireless network |
| US6973315B1 (en) * | 2001-07-02 | 2005-12-06 | Cisco Technology, Inc. | Method and system for sharing over-allocated bandwidth between different classes of service in a wireless network |
| US7349704B2 (en) * | 2001-07-02 | 2008-03-25 | Cisco Technology, Inc. | Method and system for sharing over-allocated bandwidth between different classes of service in a wireless network |
| US7257632B2 (en) * | 2001-07-30 | 2007-08-14 | Fujitsu Limited | Method and apparatus for a bandwidth broker in a packet network |
| US20030028641A1 (en) * | 2001-07-30 | 2003-02-06 | Zhi-Li Zhang | Method and apparatus for a bandwidth broker in a packet network |
| US7475141B1 (en) * | 2001-07-31 | 2009-01-06 | Arbor Networks, Inc. | Distributed service level management for network traffic |
| US10140433B2 (en) | 2001-08-03 | 2018-11-27 | Comcast Ip Holdings I, Llc | Video and digital multimedia aggregator |
| US10349096B2 (en) | 2001-08-03 | 2019-07-09 | Comcast Ip Holdings I, Llc | Video and digital multimedia aggregator content coding and formatting |
| US7787370B1 (en) * | 2001-09-06 | 2010-08-31 | Nortel Networks Limited | Technique for adaptively load balancing connections in multi-link trunks |
| US20030084144A1 (en) * | 2001-10-30 | 2003-05-01 | Lipinski Greg J. | Network bandwidth optimization method and system |
| US7237020B1 (en) | 2002-01-25 | 2007-06-26 | Hewlett-Packard Development Company, L.P. | Integer programming technique for verifying and reprovisioning an interconnect fabric design |
| US8260959B2 (en) | 2002-01-31 | 2012-09-04 | British Telecommunications Public Limited Company | Network service selection |
| US9009004B2 (en) | 2002-01-31 | 2015-04-14 | Hewlett-Packasrd Development Comany, L.P. | Generating interconnect fabric requirements |
| US20030144822A1 (en) * | 2002-01-31 | 2003-07-31 | Li-Shiuan Peh | Generating interconnect fabric requirements |
| US20060149854A1 (en) * | 2002-01-31 | 2006-07-06 | Steven Rudkin | Network service selection |
| US6947750B2 (en) * | 2002-02-01 | 2005-09-20 | Nokia Corporation | Method and system for service rate allocation, traffic learning process, and QoS provisioning measurement of traffic flows |
| US20030148768A1 (en) * | 2002-02-01 | 2003-08-07 | Naveen Kakani | Method and system for service rate allocation, traffic learning process, and QoS provisioning measurement of traffic flows |
| US20030195919A1 (en) * | 2002-03-26 | 2003-10-16 | Tatsuya Watanuki | Packet distributing system and method for distributing access packets to a plurality of server apparatuses |
| US7450507B2 (en) * | 2002-06-05 | 2008-11-11 | Lucent Technologies Inc. | Hierarchal rate-limiting at a network node that utilizes an infinity rate-limit check |
| US20080123534A1 (en) * | 2002-10-18 | 2008-05-29 | Cariden Technologies, Inc. | Metric optimization for traffic engineering in a metric-routed network |
| US7782773B2 (en) * | 2002-10-18 | 2010-08-24 | Cariden Technologies, Inc. | Metric optimization for traffic engineering in a metric-routed network |
| US20040100908A1 (en) * | 2002-11-27 | 2004-05-27 | Khosravi Hormuzd M. | Method and apparatus to provide IP QoS in a router having a non-monolithic design |
| US20040109414A1 (en) * | 2002-12-10 | 2004-06-10 | Choi Gil Young | Method of providing differentiated service based quality of service to voice over internet protocol packets on router |
| US20040205762A1 (en) * | 2003-02-24 | 2004-10-14 | Kabushiki Kaisha Toshiba | Communication control apparatus, communication control method and communication control program product |
| US20080159283A1 (en) * | 2003-02-24 | 2008-07-03 | Kabushiki Kaisha Toshiba | Communication control apparatus, communication control method and communication control program product |
| US7366785B2 (en) * | 2003-02-24 | 2008-04-29 | Kabushiki Kaisha Toshiba | Communication control apparatus, communication control method and communication control program product |
| US20080165682A1 (en) * | 2003-02-24 | 2008-07-10 | Kabushiki Kaisha Toshiba | Communication control apparatus, communication control method and communication control program product |
| US7310761B2 (en) * | 2003-04-26 | 2007-12-18 | Samsung Electronics Co., Ltd. | Apparatus and method for retransmitting data packets in mobile ad hoc network environment |
| US20040218607A1 (en) * | 2003-04-30 | 2004-11-04 | Tuija Hurtta | Handling traffic flows in a mobile communications network |
| US20080259865A1 (en) * | 2003-04-30 | 2008-10-23 | Nokia Corporation | Handling traffic flows in a mobile communications network |
| US9350566B2 (en) * | 2003-04-30 | 2016-05-24 | Nokia Technologies Oy | Handling traffic flows in a mobile communications network |
| US9319242B2 (en) * | 2003-04-30 | 2016-04-19 | Nokia Technologies Oy | Handling traffic flows in a mobile communications network |
| US20050089042A1 (en) * | 2003-10-24 | 2005-04-28 | Jussi Ruutu | System and method for facilitating flexible quality of service |
| US7092358B2 (en) * | 2003-10-24 | 2006-08-15 | Nokia Corporation | System and method for facilitating flexible quality of service |
| US7948990B2 (en) * | 2003-12-19 | 2011-05-24 | Nokia Corporation | Control decisions in a communication system |
| US20050135375A1 (en) * | 2003-12-19 | 2005-06-23 | Nokia Corporation | Control decisions in a communication system |
| WO2005081474A1 (en) * | 2004-02-25 | 2005-09-01 | National University Of Singapore | Qos in optical networks |
| US20050265359A1 (en) * | 2004-05-13 | 2005-12-01 | Drew Julie W | Optimizing switch port assignments |
| US9055550B1 (en) | 2004-08-24 | 2015-06-09 | Comcast Cable Holdings, Llc | Locating a voice over packet (VoP) device connected to a network |
| US8724522B2 (en) | 2004-08-24 | 2014-05-13 | Comcast Cable Holdings, Llc | Method and system for locating a voice over internet protocol (VoIP) device connected to a network |
| US10070466B2 (en) | 2004-08-24 | 2018-09-04 | Comcast Cable Communications, Llc | Determining a location of a device for calling via an access point |
| US9036626B2 (en) | 2004-08-24 | 2015-05-19 | Comcast Cable Holdings, Llc | Method and system for locating a voice over internet protocol (VOIP) device connected to a network |
| US9049132B1 (en) | 2004-08-24 | 2015-06-02 | Comcast Cable Holdings, Llc | Locating a voice over packet (VoP) device connected to a network |
| US10517140B2 (en) | 2004-08-24 | 2019-12-24 | Comcast Cable Communications, Llc | Determining a location of a device for calling via an access point |
| US11252779B2 (en) | 2004-08-24 | 2022-02-15 | Comcast Cable Communications, Llc | Physical location management for voice over packet communication |
| US7940746B2 (en) | 2004-08-24 | 2011-05-10 | Comcast Cable Holdings, Llc | Method and system for locating a voice over internet protocol (VoIP) device connected to a network |
| US9648644B2 (en) | 2004-08-24 | 2017-05-09 | Comcast Cable Communications, Llc | Determining a location of a device for calling via an access point |
| WO2006033514A3 (en) * | 2004-09-22 | 2006-05-11 | Ute Electronics & Telecommunications Res Inst | Internal data structure of mobile terminal for qos-based uplink data transmission, and operational methods thereof |
| US7978651B2 (en) | 2004-09-22 | 2011-07-12 | Samsung Electronics Co., Ltd. | Internal data structure of mobile terminal for QoS-based uplink data transmission, and operational methods thereof |
| WO2006033514A2 (en) * | 2004-09-22 | 2006-03-30 | Electronics And Telecommunications Research Institute | Internal data structure of mobile terminal for qos-based uplink data transmission, and operational methods thereof |
| US20060083226A1 (en) * | 2004-10-18 | 2006-04-20 | At&T Corp. | Queueing technique for multiple sources and multiple priorities |
| US7545815B2 (en) | 2004-10-18 | 2009-06-09 | At&T Intellectual Property Ii, L.P. | Queueing technique for multiple sources and multiple priorities |
| CN100337456C (en) * | 2004-11-23 | 2007-09-12 | 毛德操 | Method for raising safety of IP network through router signature |
| US20090181673A1 (en) * | 2004-12-06 | 2009-07-16 | Motorola, Inc. | Method, apparatus and base station for determining a radio link characteristic |
| WO2006062887A1 (en) * | 2004-12-09 | 2006-06-15 | The Boeing Company | Network centric quality of service using active network technology |
| US20060126504A1 (en) * | 2004-12-09 | 2006-06-15 | The Boeing Company | Network centric quality of service using active network technology |
| US7561521B2 (en) | 2004-12-09 | 2009-07-14 | The Boeing Company | Network centric quality of service using active network technology |
| US20080273461A1 (en) * | 2005-03-29 | 2008-11-06 | International Business Machines Corporation | Network system, traffic balancing method, network monitoring device and host |
| US8194553B2 (en) * | 2005-03-29 | 2012-06-05 | International Business Machines Corporation | Network system, traffic balancing method, network monitoring device and host |
| US20060248372A1 (en) * | 2005-04-29 | 2006-11-02 | International Business Machines Corporation | Intelligent resource provisioning based on on-demand weight calculation |
| US8428074B2 (en) | 2005-04-29 | 2013-04-23 | Prom Ks Mgmt Limited Liability Company | Back-to back H.323 proxy gatekeeper |
| US7793297B2 (en) | 2005-04-29 | 2010-09-07 | International Business Machines Corporation | Intelligent resource provisioning based on on-demand weight calculation |
| US7751316B2 (en) * | 2005-05-13 | 2010-07-06 | Yahoo! Inc. | Relay Server for SIP/RTP messages with buffer management |
| US20060256721A1 (en) * | 2005-05-13 | 2006-11-16 | Yahoo! Inc. | Dynamically selecting codecs for managing an audio message |
| US20070058650A1 (en) * | 2005-08-09 | 2007-03-15 | International Business Machines Corporation | Resource buffer sizing under replenishment for services |
| WO2007063431A3 (en) * | 2005-11-29 | 2007-10-18 | Cit Alcatel | Communication session admission control systems and methods |
| US9049158B2 (en) | 2005-11-29 | 2015-06-02 | Alcatel Lucent | Communication session admission control systems and methods |
| US20070121500A1 (en) * | 2005-11-29 | 2007-05-31 | Alcatel | Communication session admission control systems and methods |
| WO2007113109A1 (en) * | 2006-03-30 | 2007-10-11 | Nokia Siemens Networks Gmbh & Co. Kg | Network access control using an additional traffic class in a communication network |
| US20110116372A1 (en) * | 2006-03-30 | 2011-05-19 | Nokia Siemens Networks Gmbh & Co. Kg | Network access control using an additional traffic class in a communication network |
| US20080225889A1 (en) * | 2007-03-14 | 2008-09-18 | Cisco Technology, Inc. | Admission control for virtualized services in routers |
| US8040916B2 (en) * | 2007-03-14 | 2011-10-18 | Cisco Technology, Inc. | Admission control for virtualized services in routers |
| US20100316022A1 (en) * | 2009-06-16 | 2010-12-16 | Verizon Patent And Licensing Inc. | Communication routing |
| US8761163B2 (en) * | 2009-06-16 | 2014-06-24 | Verizon Patent And Licensing Inc. | Communication routing |
| US8706830B2 (en) * | 2009-06-19 | 2014-04-22 | Zte Corporation | Device and method for enabling hierarchical quality of service services |
| US20120102133A1 (en) * | 2009-06-19 | 2012-04-26 | Zte Corporation | Device And Method For Enabling Hierarchical Quality Of Service Services |
| US9338099B2 (en) * | 2010-11-19 | 2016-05-10 | Cisco Technology, Inc. | Dynamic queuing and pinning to improve quality of service on uplinks in a virtualized environment |
| US20140092744A1 (en) * | 2010-11-19 | 2014-04-03 | Cisco Technology, Inc. | Dynamic Queuing and Pinning to Improve Quality of Service on Uplinks in a Virtualized Environment |
| US10104010B2 (en) | 2012-08-14 | 2018-10-16 | Huawei Technologies Co., Ltd. | Method and apparatus for allocating resources |
| CN105939290A (en) * | 2012-08-14 | 2016-09-14 | 华为技术有限公司 | Resource allocation method and device |
| CN105939290B (en) * | 2012-08-14 | 2019-07-09 | 华为技术有限公司 | A kind of method and device for distributing resource |
| US9565139B2 (en) * | 2013-03-15 | 2017-02-07 | Comcast Cable Communications, Llc | Remote latency adjustment |
| US11038820B2 (en) | 2013-03-15 | 2021-06-15 | Comcast Cable Communications, Llc | Remote latency adjustment |
| EP2779544A1 (en) * | 2013-03-15 | 2014-09-17 | Comcast Cable Communications, LLC | Remote latency adjustment |
| US20140269755A1 (en) * | 2013-03-15 | 2014-09-18 | Comcast Cable Communications, Llc | Remote latency adjustment |
| US20140344473A1 (en) * | 2013-05-16 | 2014-11-20 | Power-All Networks Limited | Transmission management device, system, and method |
| US20140341033A1 (en) * | 2013-05-16 | 2014-11-20 | Power-All Networks Limited | Transmission management device, system, and method |
| US20150074234A1 (en) * | 2013-09-11 | 2015-03-12 | Electronics And Telecommunications Research Institute | Content system and method for chunk-based content delivery |
| US9413634B2 (en) * | 2014-01-10 | 2016-08-09 | Juniper Networks, Inc. | Dynamic end-to-end network path setup across multiple network layers with network service chaining |
| US20150200838A1 (en) * | 2014-01-10 | 2015-07-16 | Juniper Networks, Inc. | Dynamic end-to-end network path setup across multiple network layers with network service chaining |
| US9667482B2 (en) * | 2014-06-26 | 2017-05-30 | Fujitsu Limited | Communication apparatus and communication method |
| US20150381496A1 (en) * | 2014-06-26 | 2015-12-31 | Fujitsu Limited | Communication apparatus and communication method |
| US20170155574A1 (en) * | 2015-12-01 | 2017-06-01 | Transition Networks, Inc. | Connection qualified link pass through |
| US10666565B2 (en) * | 2018-06-08 | 2020-05-26 | Citrix Systems, Inc. | Method to measure relative QOS gains and to reduce the variance in QOS for similar connections for during bandwidth contention |
| US11510073B2 (en) * | 2020-10-23 | 2022-11-22 | At&T Intellectual Property I, L.P. | Mobility backhaul bandwidth on demand |
| US11956852B2 (en) | 2022-02-11 | 2024-04-09 | Comcast Cable Communications, Llc | Physical location management for voice over packet communication |
| CN116094992A (en) * | 2022-12-23 | 2023-05-09 | 中电信数智科技有限公司 | Message forwarding method, storage medium and device based on worksheet scene |
Also Published As
| Publication number | Publication date |
|---|---|
| US6973033B1 (en) | 2005-12-06 |
Similar Documents
| Publication | Publication Date | Title |
|---|---|---|
| US6744767B1 (en) | Method and apparatus for provisioning and monitoring internet protocol quality of service | |
| EP1851919B1 (en) | Bandwidth allocation for telecommunications networks | |
| Zhao et al. | Internet quality of service: An overview | |
| US6999420B1 (en) | Method and apparatus for an architecture and design of internet protocol quality of service provisioning | |
| US7382727B2 (en) | System and method for asymmetrical bandwidth management | |
| US7274666B2 (en) | Method and system for managing traffic within a data communication network | |
| US20100226249A1 (en) | Access control for packet-oriented networks | |
| AU2002339309B2 (en) | Traffic restriction by means of reliability check for a packet-oriented connectionless network with QoS transmission | |
| KR20060064661A (en) | Flexible admission control for different traffic classes in a communication network | |
| Mao et al. | PQWRR scheduling algorithm in supporting of DiffServ | |
| US20090304020A1 (en) | Method and Arrangement in a Data Network for Bandwidth Management | |
| US20050259689A1 (en) | Providing soft bandwidth guarantees using elastic TCP-based tunnels | |
| US7266612B1 (en) | Network having overload control using deterministic early active drops | |
| Lakkakorpi et al. | Adaptive connection admission control for differentiated services access networks | |
| Cisco | Congestion Management Overview | |
| US6778523B1 (en) | Connectionless oriented communications network | |
| Cisco | Policing and Shaping Overview | |
| Cisco | QC: Quality of Service Overview | |
| Banchs et al. | A scalable share differentiation architecture for elastic and real-time traffic | |
| Michalas et al. | Proportional delay differentiation employing the CBQ service discipline | |
| Kingston | Dynamic precedence for military ip networks | |
| Serban et al. | Dynamic resource allocation in core routers of a Diffserv network | |
| Kim et al. | QoS-guaranteed DiffServ-Aware-MPLS traffic engineering with controlled bandwidth borrowing | |
| Radivojević et al. | Quality of Service Implementation | |
| Baumgartner et al. | Differentiated internet services |
Legal Events
| Date | Code | Title | Description |
|---|---|---|---|
| AS | Assignment |
Owner name: AT&T CORP., NEW YORK Free format text: ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNORS:CHIU, ANGELA L.;CIVANLAR, SEYHAN;TANG, ZHUANGBO;REEL/FRAME:010488/0809;SIGNING DATES FROM 19991112 TO 19991116 |
|
| AS | Assignment |
Owner name: AT&T CORP., NEW YORK Free format text: ASSIGNMENT OF ASSIGNORS INTEREST;ASSIGNOR:GREENBEG, ALBERT GORDON;REEL/FRAME:011308/0734 Effective date: 19991229 |
|
| FPAY | Fee payment |
Year of fee payment: 4 |
|
| FPAY | Fee payment |
Year of fee payment: 8 |
|
| REMI | Maintenance fee reminder mailed | ||
| LAPS | Lapse for failure to pay maintenance fees | ||
| STCH | Information on status: patent discontinuation |
Free format text: PATENT EXPIRED DUE TO NONPAYMENT OF MAINTENANCE FEES UNDER 37 CFR 1.362 |
|
| FP | Lapsed due to failure to pay maintenance fee |
Effective date: 20160601 |